Avast (LON:AVST), a company best known for its antivirus and other cybersecurity products for consumers, has joined the Trust Over IP (ToIP) Foundation as a Steering Member. Avast recently acquired Evernym, a founding ToIP Steering Member, and SecureKey, a ToIP Contributor Member since 2020.
Avast’s ToIP Steering Committee member will be Drummond Reed, Director of Trust Services at Avast. Mr. Reed has served as Evernym’s Steering Committee member since the founding of ToIP in May 2020. He currently co-chairs the ToIP Governance Stack Working Group and Concepts and Terminology Working Group and is a vice-chair of the Technology Stack Working Group.
“Avast brings a new perspective to the Foundation’s mission of defining Internet-scale decentralized digital trust infrastructure,” said Mr. Reed. “Avast has a 30 year history of protecting the digital devices of over 435 million consumers. Now Avast wants to extend that protection to individual’s digital identity and relationships online because identity is at the very heart of cybersecurity.”
Avast, headquartered in Prague, is rapidly building one of the largest decentralized digital trust teams in the world. In June of 2021, they hired Charles Walton, a former Mastercard executive (and Mastercard’s original ToIP Steering Committee member), as General Manager of their new Digital Trust Services division. Then in December 2021, Avast acquired Evernym, one of the global leaders in self-sovereign identity (SSI). In March 2022 they announced the acquisition of SecureKey, operators of the Verified.Me network in Canada that is one of the largest bank ID networks in the world.
In a keynote speech at the European Identity Conference in Berlin, Mr. Walton said Avast would be focusing its efforts on the “empowered consumer”—giving individuals the tools they need to have portable, reusable digital identity credentials that do not depend on any one device, operating system, or identity federation. “It is finally time we had digital wallets with digital credentials that work exactly the same way our real-world wallets do,” said Mr. Reed. “We can take and use them anywhere to privately prove just what another party needs to know in the context of a particular transaction. We don’t have to go through any third-party gatekeeper to do this. That’s the way it should work in the digital world too.”
The challenge, of course, is interoperability—the entire raison d’etre of the ToIP Foundation. According to Mr. Reed, this is the reason that Avast intends to participate very actively in advancing the work of ToIP Working Groups. “Avast is a global company, and the #1 challenge in establishing digital wallets and credentials that work around the world is interoperability,” said Mr. Reed. “It is a key focus of the European Digital Identity Wallets initiative as well as other government-sanctioned digital wallet projects. Avast believes that the ToIP stack is the answer, and we want to help drive its completion and adoption as quickly as possible.”For more information about Avast’s digital trust services and products, please visit www.avast.com/digital-trust. For more information about the ToIP Foundation, visit our website or see the Introduction to ToIP white paper.

While many self-sovereign identity solutions offer tools for individuals, a government team from Canada is using digital trust technology to improve sustainability reporting in the natural resource sector for organizations.

The Government of British Columbia (B.C.) – a Trust Over IP (ToIP) Steering Committee Member – initiated the Energy & Mines Digital Trust (EMDT) project under the Ministry of Energy, Mines and Low Carbon Innovation (EMLI) to facilitate the transition to a resilient, clean economy. EMDT’s pilot enables a collaborative digital ecosystem between the B.C. government, natural resource companies, and organizations around the world to improve sustainability reporting using digital credentials. Digital credentials make sustainability reporting more efficient, enhance business-to-business trust, and protect data from manipulation. Digital credentials can be checked in real time, expediting access to trustworthy information. These trusted, verifiable digital credentials are the core digital trust technologies being piloted and the trust ecosystem in which they operate are defined in ToIP architecture, governance, and related documents.
Join members of the open-source community as they share projects, discuss problems, and collaborate on new solutions at three Linux Foundation conferences this September. Attend one of three sessions featuring EMDT’s business application of digital credentials with Nancy Norris, Senior Director of ESG & Digital Trust in the Ministry for Energy, Mines and Low Carbon Innovation for the Government of British Columbia, and Kyle Robinson, Senior Strategic Advisor.

- Hyperledger Global Forum, September 12: Learn how EMDT is enabling and accelerating the B.C. government’s entry into a digital trust ecosystem by creating a simple and secure way to share sustainability data, certifications, and credentials.
- Trust Over IP Summit, September 14: In Session 2, witness a demo, exchanging digital credentials between an environmental auditor, a mining company, and the Government of British Columbia. Stay for Session 4, to learn how and why digital trust ecosystems benefit government bodies.
- Open Source Summit Europe, September 15: EMDT will participate in the “Blockchain in Action in the Fight Against Climate Change” panel session with Hyperledger’s Daniela Barbosa and others to discuss the role of government in creating digital trust ecosystems and how enhanced sustainability reporting supports climate goals.
To learn more about Energy & Mines Digital Trust, be sure to include the Trust Over IP Summit as a co-located event to your Open Source Summit Europe registration and/or register for Hyperledger Global Forum.
Two weeks ago was the first full-scale Identiverse since the pandemic began, and host Ping Identity pulled out all the stops. It started off with a wonderful video splash with spotlighted drummers banging away, setting the stage for three days of wonderful entertainment, great keynotes, engaging sessions, and nonstop networking.
Ping CEO Andre Durand ‘s opening keynote set the tone by putting decentralized identity front and center. Stating that our current systems do not scale, Andre took us on a journey through the history of Identity solutions from passwords, to single sign-on, to OAuth, to centralized and federated identity.
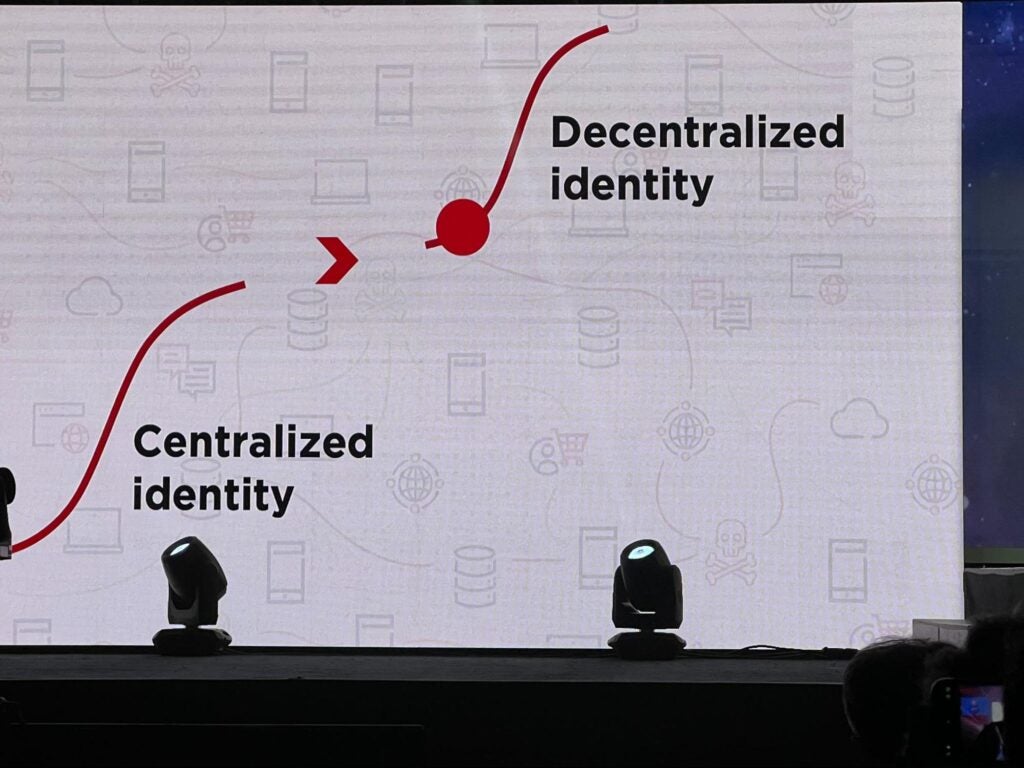
He then ended with what we all know at the Trust Over IP Foundation: that the future is decentralized identity.
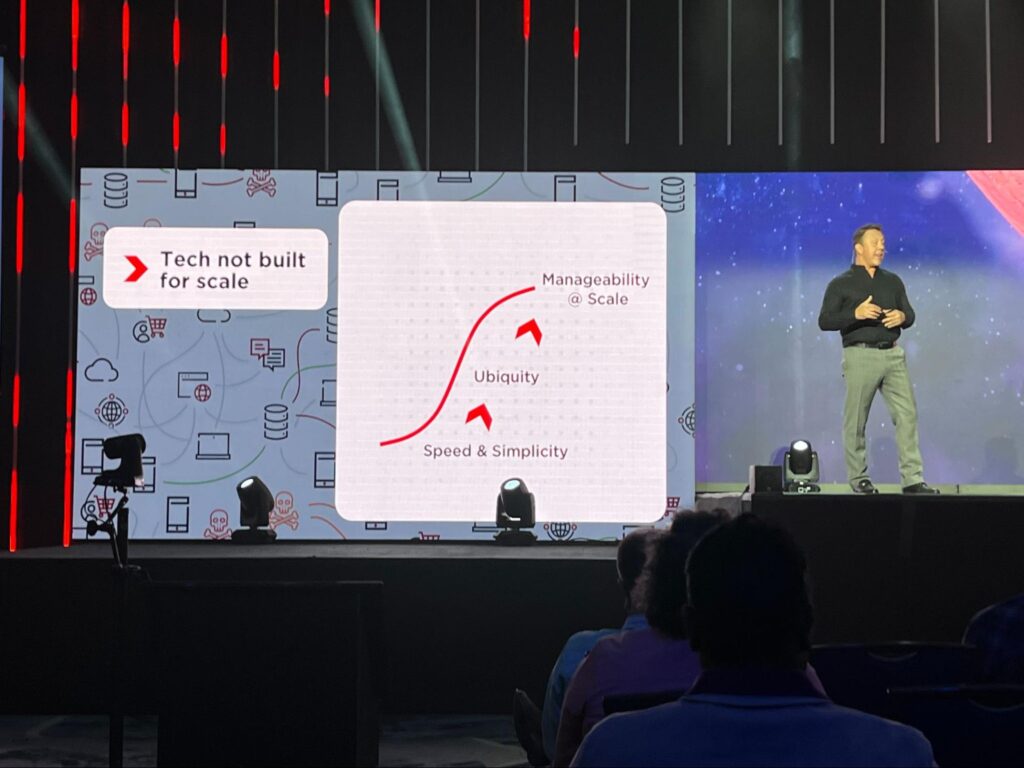
It was not just a wonderful start to the conference, but a great summary of exactly why ToIP was founded: we are collaborating to develop the recommendations, standards, guides, and templates needed to connect the gap shown on Andre’s slide above.
If there was a real surprise at this year’s Identiverse, it was the evidence presented throughout the conference that decentralized identity isn’t just the future, it is the NOW. For example, only an hour after Andre’s keynote, Kristina Yasuda, Senior Identity Standards Architecture at Microsoft, gave an entire talk extolling the virtues of verifiable credentials (VCs) without even mentioning Microsoft’s own VC products. (She also didn’t mention that she is the new co-chair of the new W3C Verifiable Credentials 2.0 Working Group along with Brent Zundel of Avast).
Shortly after Kristina’s session, Brent and Drummond Reed gave a presentation on how the SSI model of digital wallets and VCs can and should be integrated with existing identity and access management (IAM) systems. Their goal was to dispel any notion that “rip and replace” was necessary to start using VCs and the ToIP stack.
But the most resounding endorsement of VCs came when Alex Simons, Microsoft’s Corporate Vice President of Identity and Network Access gave the opening keynote on the second day. He not only spent the entire first half of his talk explaining why VCs were the headline new feature of the Microsoft Entra product suite, but then invited Kristina to give a live demo of VC interop between Microsoft, Ping, Workday, IBM, and MATTR. For more on the specific interop profile they were using, see this blog post from Microsoft decentralized identity product manager Ankur Patel.
On Thursday, ToIP Steering Committee member Mike Vesey, CEO of IdRamp presented several use cases in his session “Establishing Trust with Decentralized Identity Networks, Verifiable Credentials, and Zero Trust”. Mike shared several decentralized identity solutions operating in production today, including:
- “Zoom Bouncer”, a new meeting security application now available in the Zoom public app store that allow meeting hosts to use verifiable credentials and biometrics to protect virtual meetings from zoom bombing.
- The North Dakota Department of Education decentralized identity initiative shows how verifiable credentials are being used for decentralized verification of student learner records for graduating students.
Mike also gave a demo of the IdRamp zero code orchestration platform that allows issuance of verifiable credentials from any traditional IAM system and verification with any traditional relying party service—an entire journey that can be implemented in just a few minutes without any code. “IdRamp has been providing decentralization for a few years now.” states Mike Vesey, “The IdRamp platform provides a seamless bridge from centralized identity systems into decentralized credential based authentication and access control. It was inspiring to hear that same vision being shared by the largest IAM organizations in the world. The future of identity is decentralized and ToIP is playing a major role in guiding organizations on their journey into decentralized zero trust protection.”
Judith Fleenor, Director of Strategic Engagement at the Trust Over IP Foundation, agrees: “It’s exciting to see live use cases of verifiable credentials across various sectors of government and industry. It is equally exciting to see organizations such as our Steering Committee members IdRamp and Monokee making integration with traditional IAM a breeze through their innovative system integration platforms and consulting services.”
Another key theme throughout the conference was FIDO2 passkeys. At least a half-dozen sessions were focused on this topic—not surprising given the announcements from Apple, Google, Mozilla, and the FIDO Alliance earlier this spring—and that Identiverse focuses on an enterprise IAM-centric audience where solutions to multi-factor and passwordless authentication have been sought after for two decades.
Overall, the attendees from ToIP agreed that this Identiverse took a strong step in the direction of ToIP—and it made it even more important that we push forward with our work of completing the full definition of the ToIP stack.
If you’d like to participate in ToIP’s efforts to further define a complete governance and technical architecture for interoperable digital trust, join us by becoming a member.
We are pleased to announce that Monokee s.r.l., a scaleup from north Italy, has joined the ToIP Foundation as a Steering Member. A company rising from the centralized and federated IAM world to embrace the SSI paradigm, Monokee intends to be an active contributor to the community’s efforts in defining the interoperability standards that will lead to Web 3.0.
Launched in 2018, Monokee leverages the 20 years of experience of its two founders in IAM/IGA consulting. The company’s flagship product is an easy-to-integrate, point-and-click visual identity orchestration tool used by security architects from SMEs to larger enterprises.
Representing Monokee on the Steering Committee will be Ing. Roberto Griggio, Monokee’s CEO. Roberto graduated in Computer Science from the University of Venice, Italy and sports more than 20 years in identity and access management and related fields. On the technical working groups and task forces, Monokee will be represented by Dr. Mattia Zago, Monokee’s SSI Solutions Architect. Mattia holds a Ph.D. from the University of Murcia, Spain, specifically dedicated to cybersecurity and artificial intelligence subjects.
“Joining the ToIP Steering Committee represents a significant milestone for me as a researcher and us as an identity company,” said Dr. Zago. “Seeing that the community is aligned with our view of a hybrid integration between federated enterprises’ services and decentralized identities further increases our motivation to pursue it. Indeed, we will keep pushing forward our identity orchestrator to provide seamless (and codeless) integration experiences for security engineers.”
Monokee believes a formal definition for the authentication and authorization processes is critical for integrating IAM/IGA solutions. Despite the importance of this aspect, most contemporary solutions require a non-negligible amount of engineering effort to connect identities, attributes, applications, flows, protocols, and many other elements.
Monokee simplifies this process with its Visual Identity Orchestrator (VIO), a drag-and-drop interface to build your authentication processes from scratch, starting from predefined blocks and connecting them in a flow-chart fashion as illustrated below.
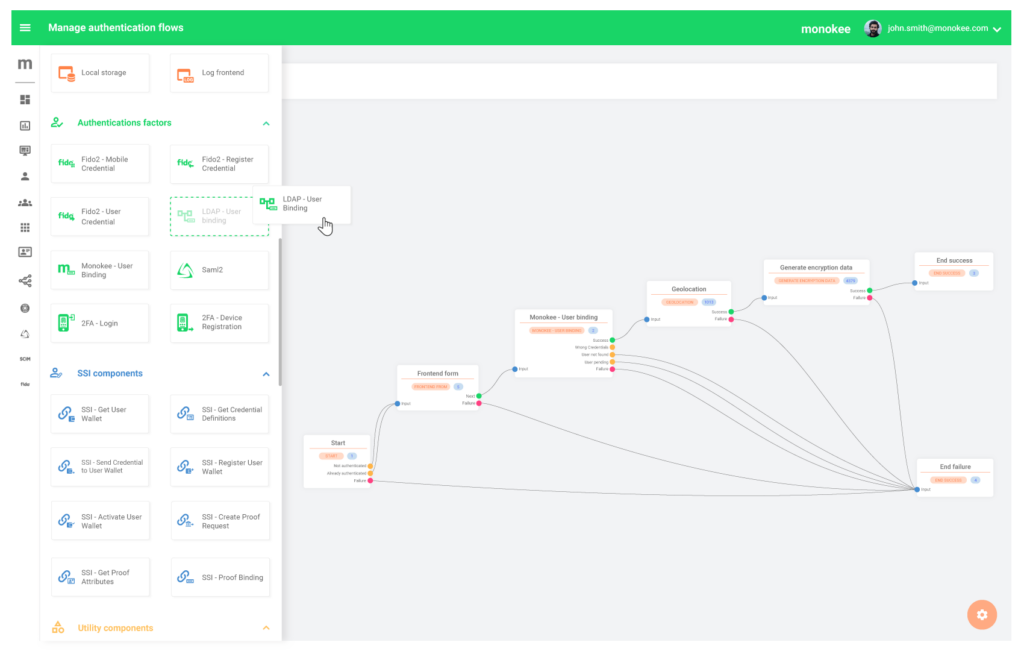
Each block and connector in the resulting map represent parts of the process in a virtually codeless environment: Monokee’s visual builder turns that map into computer-generated code, with no room for human errors. The VIO is also a major improvement for process management. For example, adding an authentication factor in an existing process is just a matter of dragging a new block into the chart and inserting it into the flow.
The abstraction provided by Monokee’s VIO aligns perfectly with the vision of the ToIP foundation of an interoperable web of trust. Specifically, Monokee aims to bridge the gap that exists at layers 3 and 4 of the ToIP stack between classic centralized and federated ecosystems and new decentralized services and resources. While this obviously involves technical challenges, the real interoperability questions reside in the governance framework that coordinates the topmost ecosystem layer: how to embrace the new trust paradigm without tossing away the achievements of the last decade?
Monokee envisions a hybrid world capable of taking advantage of the structured, well-tested, and effective IAM solutions while incorporating decentralized and distributed elements to improve end-user privacy and usability. Monokee plans to provide resources and workforce to help ToIP working groups achieve their 2022 objectives, starting with the ToIP Technology Architecture Specification, anticipated for release in September 2022.
Two of the most influential global membership organisations in the digital ID space have aligned to forge a faster and more secure route to a shared and trusted digital future.
Both The Open Identity Exchange (OIX) and Trust over IP Foundation (ToIP) have driven key development and made significant progress in their respective communities towards addressing the challenges around establishing ‘trust’ in users via digital means.
They have now committed to aligning their efforts, having realised the synergies in the work they were doing and the vast potential of working more closely together to drive their common agenda across the globe.
With a combined worldwide membership of over 400 organisations and individuals, including some of the world’s largest stakeholders in a digital ID future, this is a crucial development in the journey towards full digital ID adoption and a digital future that will work for everyone involved.
Born from the self-sovereign identity movement, ToIP’s widely recognised ToIP Stack is defining a complete architecture for internet-scale digital trust that combines the technical requirements for cryptographic trust at the machine layer with the governance requirements for human trust at the business, legal, and social layers.
Equally, the OIX’s comprehensive work around the governance of digital ID has been highly influential and widely accepted. It complements the governance elements of the ToIP stack. A prime example is OIX’s recently launched Guide to Trust Frameworks for Smart Digital ID that encompasses over 10 years of research and in-depth evaluation of existing Trust Frameworks around the world.
The Guide outlines how a both a simple digital ID (i.e., digitised credentials within a wallet) and a smart digital ID (i.e., one that understands rules to “to selectively disclose, derivate a specific attribute and aggregate several single attributes” per the EU’s new eIDAS2 ARF) can meet the needs of all the parties involved in a digital relationship or transaction. With a specific focus on placing the needs of the end users at the forefront (also a key driver for ToIP), the Guide defines the roles, responsibilities, principles, policies, procedures and standards needed.While remaining technology agnostic, a particular feature of the Guide is its alignment with the self-sovereign paradigm of decentralized identifiers (DIDs) and verifiable credentials stored in individual digital wallets. The Guide includes a mapping of OIX Trust Framework roles to SSI Roles as illustrated in the infographics below.
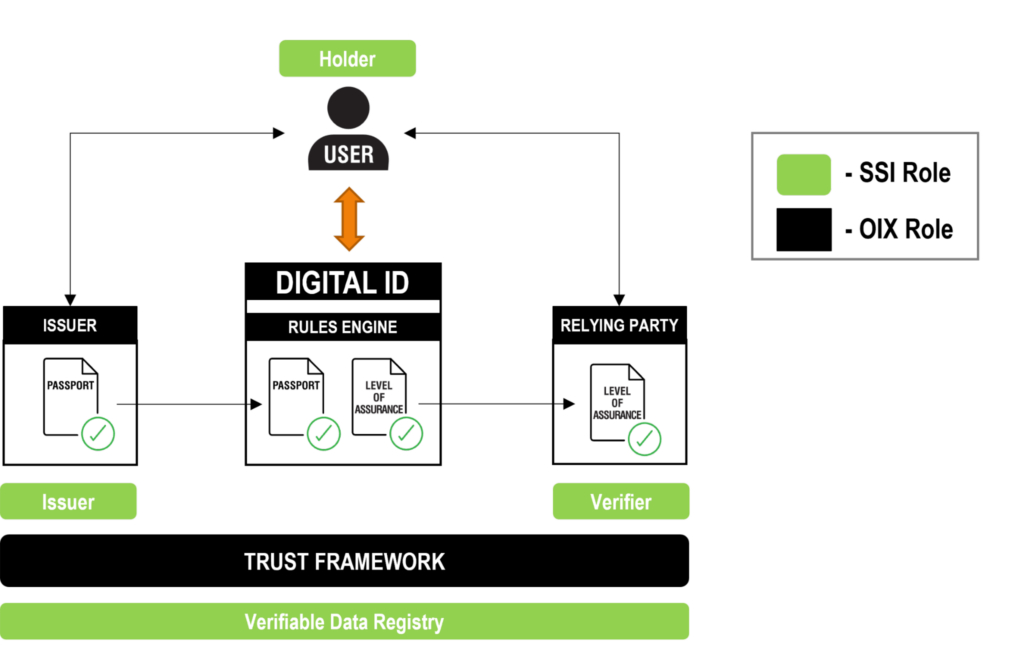
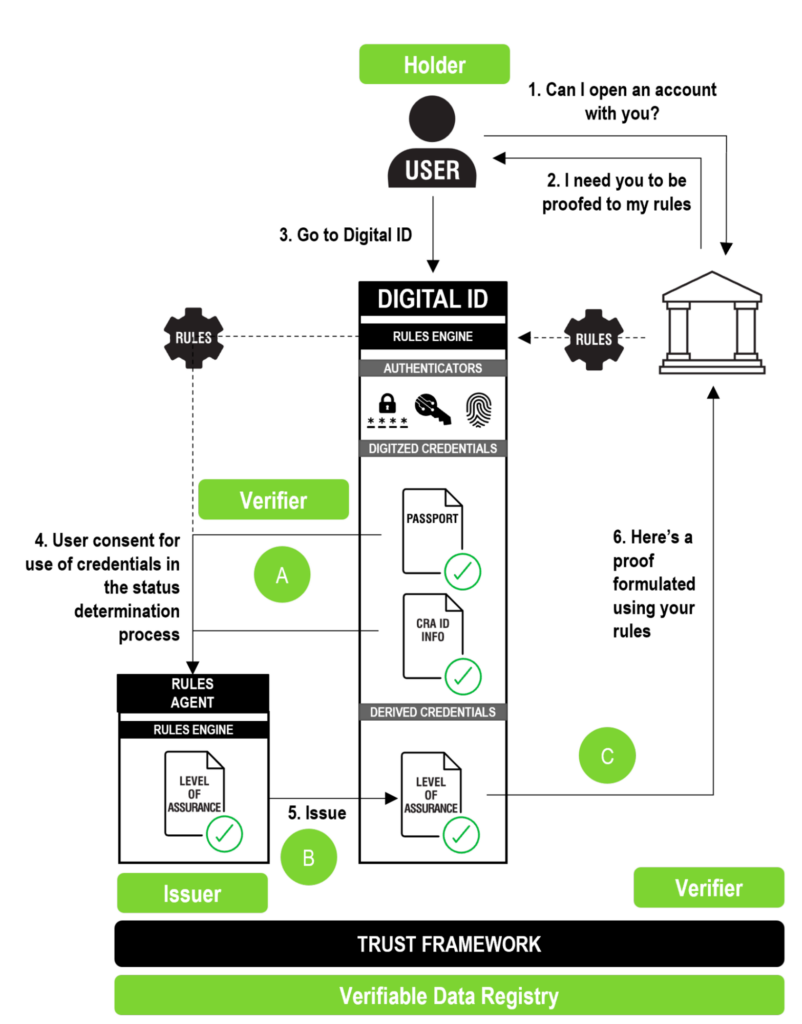
While this first infographic illustrates the relatively straightforward mapping of the SSI issuer/holder/verifier “trust triangle”, the Guide also shows how to map more complex SSI scenarios such as the one below, in which a holder submits proofs of one set of credentials to a rules engine to obtain a new derived level-of-assurance credential.
John Jordan, Executive Director of ToIP, said: “The lack of globally interoperable digital trust infrastructure has presented an urgent and widely acknowledged need for both technical standards and governance that ensure trust can be established quickly and safely across all sectors and borders. Our two organisations have a common vision – building trust online, and simplifying and standardising how trust is established. Our collective knowledge, expertise and research will be a powerful force ensuring the benefits of digital ID are realised by everyone involved – the end consumers, governments, relying parties and ID providers.”
Nick Mothershaw, Chief Identity Strategist at OIX, said: “Various initiatives around the world are trying to address the same issue with differing approaches. It is a highly complex global challenge that needs a united global response, and one that ensures the needs of all parties are met. To achieve it, governance must be generic and technology agnostic, and smart digital ID will need to play a significant role. The goals and strategies of both organisations highly complement each other. We have both already made significant progress, which has been reflected in the growth of our memberships, and the Self-sovereign alignment of the new OIX trust framework. By further aligning our efforts, we can have a greater impact.”
ENDS
For more information, please contact Serj Hallam
E: communications@openidentityexchange.org
T: 07789372771
About The Open Identity Exchange (OIX)
The OIX is a non-profit trade organisation on a mission to create a world where everyone can prove their identity and eligibility anywhere through a universally trusted ID. OIX is a community for all those involved in the ID sector to connect and collaborate, developing the guidance needed for inter-operable, trusted identities. Through our definition of, and education on Trust Frameworks, we create the rules, tools and confidence that will allow every individual a trusted, universally accepted, identity.
About The Trust over IP Foundation (ToIP)
As a Joint Development Foundation project of the Linux Foundation, the mission of the ToIP Foundation is to simplify and standardise how trust is established over a digital network or using digital tools. The ToIP model is a complete architecture for decentralized digital trust infrastructure that combines cryptographic verifiability at the machine layers with human accountability at the legal, business, and social layers. ToIP is a collaborative community of international experts working together to design the specifications, recommendations, guides, and tools for using the ToIP four-layer dual stack of technology and governance.

EIC 2022, held May 10-13 at the the Berlin Conference Center, had a strong ToIP presence, including Director of Strategic Engagements Judith Fleenor and Steering Committee members André Kudra (esatus), Bryn Robinson-Morgan (Mastercard), Christine Leong (Accenture), Drummond Reed (Avast), Mike Vesey (IDRamp), and Scott Perry (Schellman). Other ToIP members in attendance included Trinsic, IDunion, and Sezoo.
Our first collective takeaway was that identity conferences are back! This was the first full-scale EIC since 2019, and although still in hybrid form, in-person attendance was very strong. Vendor booths and conference sessions were quite busy, and there were four full tracks on content from midday Tuesday through Friday. “EIC was a wonderful opportunity to connect with colleagues old and new, with a shared mission to advance digital trust.” remarked Bryn “I was impressed by the interest in the ToIP stack and the recognition that to achieve interoperability on a global scale we must address both technology and governance issues.”
Our second major takeaway was that decentralized identity is a very hot topic. One of the four conference session tracks was devoted entirely to this new branch of the industry, and references to SSI and verifiable credentials were sprinkled throughout the keynotes. André noted: “Federated identity solutions are broadly used globally today and it’s great that there’s now such huge interest to infuse SSI to it. To ultimately arrive at a truly decentralized online identity world, embracing what’s already out there is inevitable.”
On that note, Judith spotted numerous examples of SSI terminology being “co-opted” to describe products and services that did not in fact follow SSI and ToIP design principles. This is both a good thing (because the speakers wanted to be associated with SSI) and a bad thing (because they are mis-using the terms).
A third major takeaway was that the world of federation wants to join the world of decentralization. One of the major announcements from the conference was the OpenID Foundation white paper entitled OpenID for Verifiable Credentials. To quote from the OpenID website:
The goal of this whitepaper is to inform and educate the readers about the work on the OpenID for Verifiable Credentials (OpenID4VC) specifications family. It addresses use-cases referred to as Self-Sovereign Identity, Decentralized Identity, or User-Centric Identity.
This theme was further reinforced by a series of sessions on GAIN, the Global Assured Identity Network, whose original white paper described it as an OpenID “federation of federations” that aims to bring “roaming” to existing bank ID networks around the world. At EIC, GAIN was working hard to “broaden the tent”, inviting Judith to join their final panel with 11 different speakers talking about the GAIN vision of a globally interoperable network for high-value digital identity credentials.
Judith did a wonderful job speaking to how that vision aligns with ToIP’s mission while advocating that, while federation technologies like OpenID are fine for enterprise usage, true global interoperability can best be achieved with a network of networks based on the ToIP protocol stack. She summarized the benefits of using standardized protocols rather than technical API specifications as: “OIDC for the enterprise, ToIP for the Internet”.From a ToIP perspective, the highlight was our 40-minute panel called “The Stack, the Stack, the Stack: How ToIP is Enabling Internet-Scale Digital Trust”. Judith moderated the panel consisting of André, Bryn, Christine, and Drummond sitting in front of a full-screen image of the ToIP stack.

The session drew a packed audience, and this panel format proved to be a very effective way to share the ToIP vision. At the close of the panel, we were swamped with many more questions than we had time for. We spent the next 45 minutes outside the room talking with attendees about the ToIP stack, the ToIP Foundation, and how our solution to interoperability can be applied to the European Digital Identity Wallets initiative.
This strong interest in ToIP reflects our final major takeaway from the conference: the European Digital Identity Wallets initiative is generating intense interest in interoperability. Many EIC sessions touched on different facets of the interoperability questions facing the “toolbox teams” from each of the 27 EU member states working to develop their own digital wallets. Furthermore, these questions are not limited to technical interoperability—governance is also a major concern.
“The privacy-preserving and citizen-empowering advantages of decentralized identity and verifiable credentials are clearly what is driving the EU initiative,” said Governance Stack Working Group co-chair Scott Perry. “However much of their thinking on governance is still rooted in federation technologies, so this is an area where ToIP’s work on governance frameworks can really help.”
As a final highlight, Italian digital identity company Monokee, whose Solutions Architect Dr. Mattia Zago presented on “Hybrid Central/Decentralized Identity: Deployment strategies for SSI”, was impressed enough by the ToIP presence at EIC that by the end of the conference Monokee had joined as our newest Steering Committee member.
“Joining the ToIP SC represents a significant milestone for me as a researcher and us as an identity company,” said Dr. Zago. “Seeing that the community is aligned with our view of a hybrid integration between federated enterprises’ services and decentralized identities further increases our motivation to pursue it. Indeed, we will keep pushing forward our identity orchestrator to provide seamless (and codeless) integration experiences for security engineers.”
Welcome Monokee!
by Mike Vesey, CEO, IdRamp, and Karl Kneis, COO, IdRamp


Understanding the decentralized identity (DCI) market can be challenging. Inspiring C-level decision makers and IT executives to adopt decentralized identity technology is even more difficult. Current research publications provide limited insight with inconsistent ideas and terminology. Anyone interested in DCI adoption can quickly get lost in an ocean of information that raises more questions than answers. What is the solution? Decentralized ID, Self-sovereign ID, Blockchain ID, Web 3.0 ID, Personal ID, Verifiable Credentials, DID or are they all the same thing? Is the technology production-ready or a next-generation innovation to be considered in the future?
After spending a great deal of time working with enterprise C-level teams on complex digital identity problems, one thing seems clear. When it comes to decentralized identity solutions, many business sponsors do not yet understand how DCI can provide practical answers to immediate frontline business problems. This climate creates the impression that decentralized identity is interesting but not ready for prime time adoption.
Business leaders want to know
Business leaders want to know:
- How can I use decentralization to make identity management easy to deploy and operate?
- Is it possible to add new features and business requirements without investing in long, expensive projects?
- How do I adapt this new technology without re-platforming every few years?
- Is it possible to enable decentralized identity with the systems I have to grow it at a speed and cost I can afford?
Prominent decentralized identity initiatives are often presented as pilots or innovation projects. Popular decentralized identity community discussions prioritize solving large social problems over business solutions that drive mass adoption. Understandable for a new bleeding edge technology, but the good news is DCI technology is ready for mainstream adoption now. With careful listening, collaboration and education, we can dispel misunderstanding and help business sponsors understand that decentralized identity is the best possible solution for problems they have today.
Most C-level executives do not understand the complexities of SAML or OIDC, but they do understand that solutions using these protocols help solve their business problems. We need decentralized identity to reach that same level of understanding in terms of reliability, comfort, and adoption.
Decentralized Identity needs to become ID
Shifting the conversation to the perspective of people who actually buy technology is an effective way to speed up adoption. Business leaders need proof of value, battle testing, and technical maturity. Decentralization will prevail based on measurable business results. DCI is not in battle with centralized systems; it is simply a better business solution for modern problems.
Focusing on familiar business performance indicators goes a long way in moving DCI out of the innovation lab and into mainstream adoption. Does decentralized identity help me save or make money? Is it more expensive than what I have today? When a business spends millions per year on centralized SSO and learns how decentralized identity based authentication can solve the same problem with stronger protection at less cost. That business will find value and interest in DCI adoption.
Ultimately, decentralized identity needs to become digital ID in the minds of business leaders. Trust architecture needs to be easy to understand and use. Businesses do not have time to navigate the ideology and technical complexities. They need education that speaks directly to their business problems today. Trust Over IP (TOIP) models, guides,and specifications are powerful business tools to help drive learning, transformation and adoption. You can use the growing list of free information published on the TOIP Deliverables page to help educate and transform your organization through DCI.
Perception is reality
A few common misunderstandings that come up in our business adoption conversations include:
- Decentralized identity is not just a solution for social issues, it is pain relief for front line business problems. Decentralized identity will provide superior results if you need Zero Trust, Password elimination or fraud prevention.
- Decentralized identity does not equal loss of control. It is a more effective way to manage and protect digital business.
- Decentralized identity adoption does not require re-platforming and heavy investment in line with past ID platforms. We can quickly deploy it with incremental adoption and easily combine it with all other ID services.
- Decentralized identity governance complements existing IT operation models and standards. It does not require a total change to current procedures.
- Decentralized identity service management does not require significant HR changes, custom development skills, or advanced technology resources. Existing IT teams can easily deploy and operate DCI systems with the people they have today.
That all sounds simple enough to explain, but how do you make it happen? Business sponsors need evidence to justify the investment. They need to see it in action. Our next post will focus on how we help overcome decentralized identity adoption through decentralized orchestration. This simple but powerful strategy provides an easy path for adoption and innovation.
Stay tuned.
Tampa-based Schellman, a leading provider of attestation and compliance services, announced today that it is joining the Trust over IP Foundation (ToIP) as a Steering Committee member. As the first IT audit firm to join the leadership of ToIP, this move represents Schellman’s belief in the growing suite of digital governance specifications and tools being developed by ToIP Working Groups.
Representing Schellman on the Steering Committee will be Scott Perry, whose firm Scott S. Perry CPA, PLLC, was recently acquired by Schellman. Scott was a founding Contributing Member of ToIP and has served as co-chair of the ToIP Governance Stack Working Group since its inception in May 2020.
“This is the culmination of work that began over six years ago when I started collaborating with Timothy Ruff, co-founder of Evernym and of the Sovrin Foundation, on audit and compliance in the emerging SSI space,” said Scott. “We realized that this could revolutionize how digital trust works everywhere on the Internet, and out of that was born the ToIP Foundation. So it is very gratifying for me to now join the Steering Committee and contribute directly to the success of the ToIP model.”
Scott has authored or co-authored a number of deliverables from the ToIP Governance Stack WG including:
- ToIP Governance Metamodel Specification (PDF) and Companion Guide (PDF)
- ToIP Risk Assessment Worksheet Template (Excel) and Companion Guide (PDF)
- ToIP Trust Assurance and Certification Controlled Document Template (Excel) and Companion Guide (PDF)
- ToIP Trust Criteria Matrix Template (Excel) and Companion Guide (PDF)
Scott saw the acquisition of his firm as a means of harnessing a well-established delivery capability of digital trust audit services from a top CPA Firm; Schellman saw this as a quick entry into an important emerging segment of the compliance marketplace and wanted to cement this commitment by joining the ToIP Steering Committee.
“Holding digital trust actors accountable in any or all layers of the ToIP stack will require independent audit skills and experience in a variety of compliance frameworks,” said Avani Desai, CEO at Schellman. “The deliverables already published by ToIP serve as an audit methodology for trust assurance, so they will nicely complement the services we currently offer as a WebTrust CPA firm, an ISO Certification Body, a PCI Qualified Security Assessor Company, a HITRUST assessor, a FedRAMP 3PAO, and as one of the first CMMC Authorized C3PAOs.”
“I am very happy to see this recognition of the ToIP Foundation’s groundbreaking work in digital governance frameworks,” said Judith Fleenor, ToIP Director of Strategic Engagements. “Scott has been a leader in this work from the start, and the acquisition of his firm and the support of Schellman signals that the ToIP governance metamodel is starting to see serious traction in the market. Look for more evidence coming from several new digital trust ecosystems later this year.”
Visit the Schellman website to learn more about their new Crypto and Digital Trust Service practice.