When it was launched in May 2020, the ToIP Foundation summarized its mission in a single 20-page white paper called “Introduction to Trust Over IP”. This paper was based on an article called The Trust Over IP Stack published in the December 2019 special issue of IEEE Communications Standards Magazine called The Dawn of the Internet Identity Layer and the Role of Decentralized Identity.
Two years later, with ten times more members and double the original number of working groups, the Foundation is a much more mature organization. Despite this growth, we are very pleased that the original vision of the ToIP stack has stood the test of time.
In summer of 2021, we put out a call to all ToIP members to participate in a series of “community writing workshops” to collaboratively produce two new Foundation-wide deliverables:
- Introduction to ToIP V2.0 (PDF)
This is the second-generation version of our original introductory white paper that would go more deeply into the origin and purpose of the ToIP stack and how it addresses the key challenges of decentralized digital trust infrastructure. - Design Principles for the ToIP Stack V1.0 (PDF)
This is an articulation of the key design principles we must follow in the design and development of all aspects of the ToIP stack.
We were thrilled that over two dozen members took us up on this challenge to participate over four months to produce these two documents, both of which have just been approved by the ToIP Steering Committee.
Introduction to ToIP V2.0
Our primary goal with this second-generation white paper was to make the vision and mission of ToIP accessible to a general audience—literally anyone who cares about the future of the Internet and how we can deal with the myriad security, privacy, data protection, and data sovereignty issues that have emerged as “the world’s greatest information utility” passes its first half-century of growth.
Our second goal was a “plain English” explanation of the overall structure of the four-layer, two-half sided ToIP stack using new graphics based on the wonderful interactive version developed by Peter Stoyko of Elanica. Here is the new static version of the diagram:
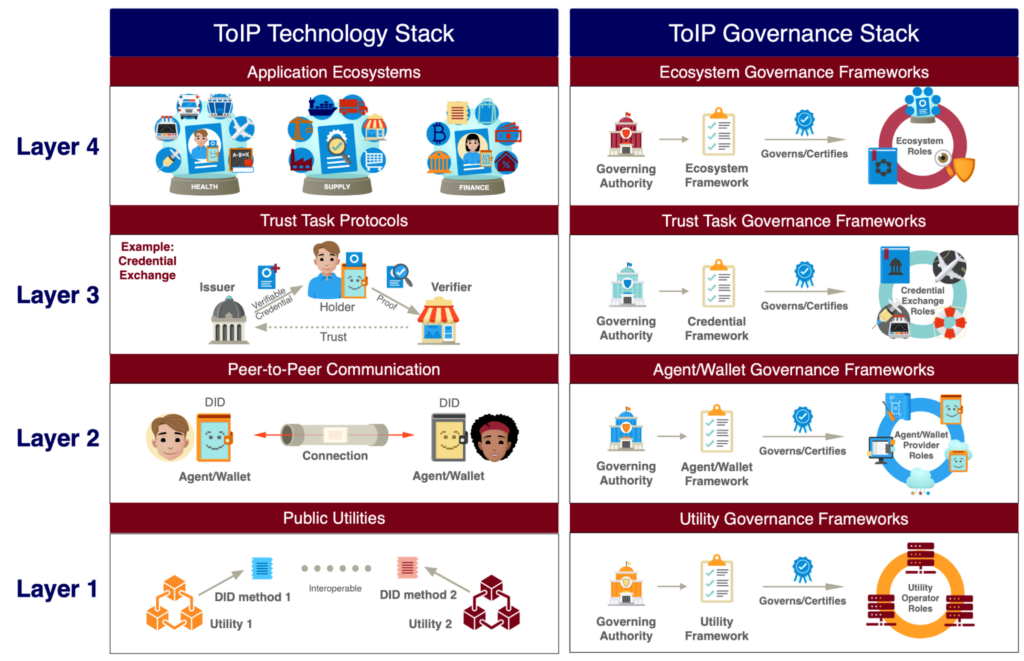
Our third goal was to provide a more complete introduction to the ToIP Foundation as a collaborative organization devoted to the design, development, adoption, and promotion of the ToIP stack—a guide to helping prospective members understand how and why to engage.
The resulting document is divided into the following sections:
- ToIP in a Nutshell
- Why Has Digital Trust Become Such a Major Problem?
- The ToIP Model for Digital Trust
- Applying This Model to the Digital World
- The ToIP Stack
- The ToIP Foundation
- How to Engage with the ToIP Foundation
- The Road Ahead
It is available as a PDF document here and on the homepage of the ToIP Foundation website.
Design Principles for the ToIP Stack V1.0
To establish a truly interoperable decentralized digital trust layer for the Internet as a whole, meticulous attention must be paid to the design of the ToIP stack. Given the tremendous growth of the ToIP Foundation—from 27 original founding member organizations to over ten times as many today—it was critical to form a strong consensus among the new members about the principles governing this design.
Another key reason to establish design principles for the development of a system is summarized in this quote from the start of the document:
The goal of any design principle is to provide guidance to the designers of a product, service, or system so they can take advantage of lessons learned from the success or failure of previous designs. Design principles represent accumulated wisdom that falls in between the generality of scientific laws and the specialization of best practices.
When it comes to a layered architecture for both technology and governance of decentralized digital trust infrastructure, the “lessons learned from the success or failure of previous designs” is prodigious. Thus the writing workshops for this document continued for four months in order to bring all the relevant design principles together.
To organize the final set of 17 principles into a logical progression, we followed a rubric suggested by co-editor Victor Syntez based on a 2006 blog post by cryptography pioneer Nick Szabo. Szabo distinguished between two types of “code”:
- Code written in a computer language expected to be executed by a machine (“dry code”), and
- Code written in a human language, i.e., laws, regulations, rules, policies and other forms of governance expected to be followed by humans (“wet code”).
Accordingly, we divided the principles into three categories:
- Principles of computer network architecture—these “dry code” principles represent fundamental lessons learned about the design of large-scale computer networked systems, especially the Internet:
#1: The End-to-End Principle
#2: Connectivity Is Its Own Reward
#3: The Hourglass Model
#4: Decentralization by Design and Default
#5: Cryptographic Verifiability
#6: Confidentiality by Design and Default
#7: Keys at the Edge
- Principles of human network architecture—these “wet code” principles represent fundamental truths about how trust relationships operate between humans—either individually or in groups:
#8: Trust is Human
#9: Trust is Relational
#10: Trust is Directional
#11: Trust is Contextual
#12: Trust has Limits
#13: Trust can be Transitive
#14: Trust and Technology have a Reciprocal Relationship
- Overall design principles—these three remaining principles apply to the overall design of the ToIP stack, “wet or dry”:
#15: Design for Ethical Values
#16: Design for Simplicity
#17: Design for Constant Change
Care was taken to not only explain each principle in plain English, but to analyze how it applies to the design of the ToIP stack at each layer. We summarized those recommendations using this table format:
| Layer | Relevance | Explanation |
| The ecosystem symbol represents the purpose of Layer 4 to support the applications needed to develop and sustain entire digital trust ecosystems. | ||
| The triangle symbol represents the Layer 3 verifiable credential “trust triangle” of issuer, holder, and verifier that enables parties using the ToIP stack to establish transitive trust. | ||
| The symbol of two connected mobile phones represents the purpose of Layer 2 as a universal peer-to-peer secure privacy-routing DID-to-DID communications protocol. | ||
| The anchor symbol represents the purpose of Layer 1 public key utilities to provide strong anchors for Decentralized Identifiers (DIDs) and their associated public keys. |
For each principle, in the “Relevance” column we assigned star ratings for each layer as follows:
| ★★★★★ | Highly relevant to the design of this layer |
| ★★★★ | Very relevant to the design of this layer |
| ★★★ | Moderately relevant to the design of this layer |
| ★★ | Somewhat relevant to the design of this layer |
| ★ | Only slightly relevant to the design of this layer |
Once all 17 principles had been compiled into a document with this format, the contributors felt that we had identified the “center of gravity” of the design of the ToIP stack that could now guide our work in completing it.
We strongly recommend this document for anyone who wants to deeply understand the rationale for our work at the ToIP Foundation. It is available as a PDF document here and on the homepage of the ToIP Foundation website.
Acknowledgments
Our thanks to Victor Syntez and Drummond Reed for serving as co-editors for these two documents and to the following ToIP members who contributed their time and expertise:
| Introduction to ToIP V2.0 | Design Principles for the ToIP Stack 1.0 |
| Carly Huitema Daniel Bachenheimer — Accenture Darrell O’Donnell — Continuum Loop Jacques Bikoundou Judith Fleenor — Trust Over IP Foundation Kaliya Young — COVID-19 Credential Initiative Karen Hand — Precision Strategic Solutions Karl Kneis — IdRamp John Jordan — Province of British Columbia Lynn Bendixsen — Indicio P. A. Subrahmanyam — CyberKnowledge Sankarshan Mukhopadhyay — Dhiway Networks Scott Perry — Scott S. Perry CPA, PLLC Vikas Malhotra — WOPLLI Technologies Wenjing Chu — Futurewei | Antti Kettunen Daniel Bachenheimer — Accenture Daniel Hardman — SICPA Darrell O’Donnell — Continuum Loop Jacques Bikoundou Jo Spencer — 460degrees John Jordan — Province of British Columbia Jonathan Rayback — Evernym Judith Fleenor — Trust Over IP Foundation Lynn Bendixsen — Indicio Mary Lacity — University of Arkansas Michel PlanteNeil Thomson — QueryVision P. A. Subrahmanyam — CyberKnowledge Rieks Joosten — TNO Sankarshan Mukhopadhyay — Dhiway Networks Scott Perry — Scott S. Perry CPA, PLLC Steven McCown — Anonyome Labs Thomas Cox Vikas Malhotra — WOPLLI Technologies Vinod Panicker — Wipro Ltd Wenjing Chu — Futurewei |
by Jan Lindquist, Neil Thomson, Burak Serdar, Paul Knowles, Christoph Fabianek, Phil Wolff
Introduction
Europe’s Data Governance Act (DGA) reached a milestone. The European Parliament announced it “…reached a provisional agreement on a new law to promote the availability of data and build a trustworthy environment to facilitate its use for research and the creation of innovative new services and products.”
What does the Data Governance Act mean to the ToIP framework and the SSI community?
Background
The DGA defines an “intermediary” that facilitates processing and sharing of data for individuals and organizations to “…increase trust in data intermediation services and foster data altruism across the EU”. In the MyData framework for user-controlled data sharing, intermediaries are called MyData Operators and there is a certification program in place. (See references at the end of this blog post.)
The DGA intermediary has a trusting relationship with the individual. There cannot be any conflict of interest in sharing the data from the individual. In the eyes of the Act, the sharing of the data shall foster “data altruism” across the EU.
To achieve this goal, DGA provisions a certification program and rules for some public-sector data.
SSI Data Sharing Models
The Data Governance Act introduces new roles into data sharing and will set up the necessary governance for a more transparent and accountable data economy. Two main actors are introduced called Data Sharing Service or Intermediaries [refer to chapter III, Requirements Applicable to Data Sharing Service in Data Governance Act] and Data Altruistic Organizations [refer to chapter IV, Data Altruistic in same reference].
Neither of these actors shall have a financial incentive that conflicts with representing a Data Subject when personal data is made available to Third-parties or Data Using Service. The following diagram has three SSI data sharing models.
A business or organization collects personal data and shares it with a third-party often in proprietary and closed interfaces. A non-proprietary health care data exchange interface is FHIR from HL7 which created an open interoperable standard.
A cooperative or intermediary represents the individual when sharing personal data. The sharing shall be standardized and interoperable between different suppliers.
A non-profit organization, acting altruistically, facilitates sharing of data that are in the public institution’s domain. The public institutions may, for example, be health care systems.
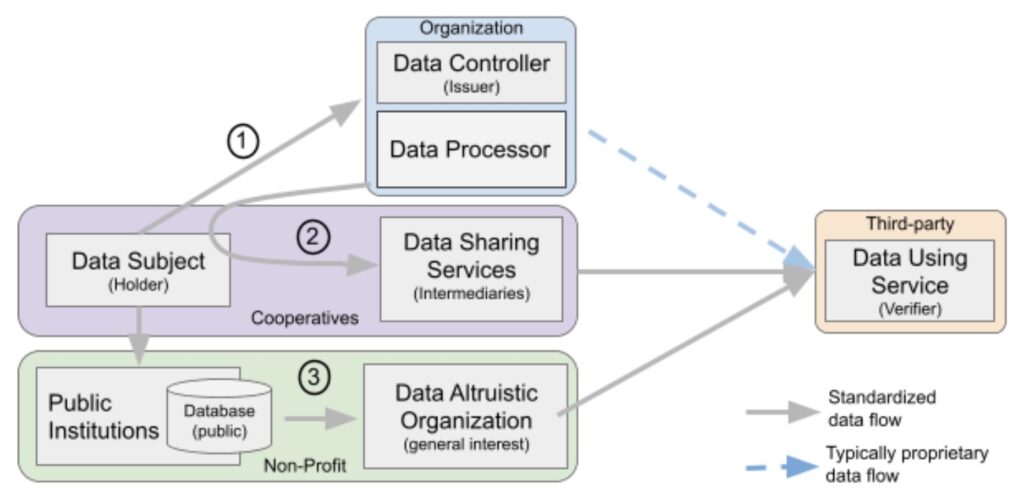
Some similarities can be drawn with the Verifiable Credential model where the Data Subject is a Holder, an organization is the Issuer and a third-party is a Verifier.
The DGA adds intermediaries to the ToIP framework
The key difference is addition of the Intermediary. The Intermediary represents an agent for the Holder (Data Subject) which has direct control of processing of personal data through a policy engine. Figure 1 shows the ToIP framework with the actors introduced in the Data Governance Act.
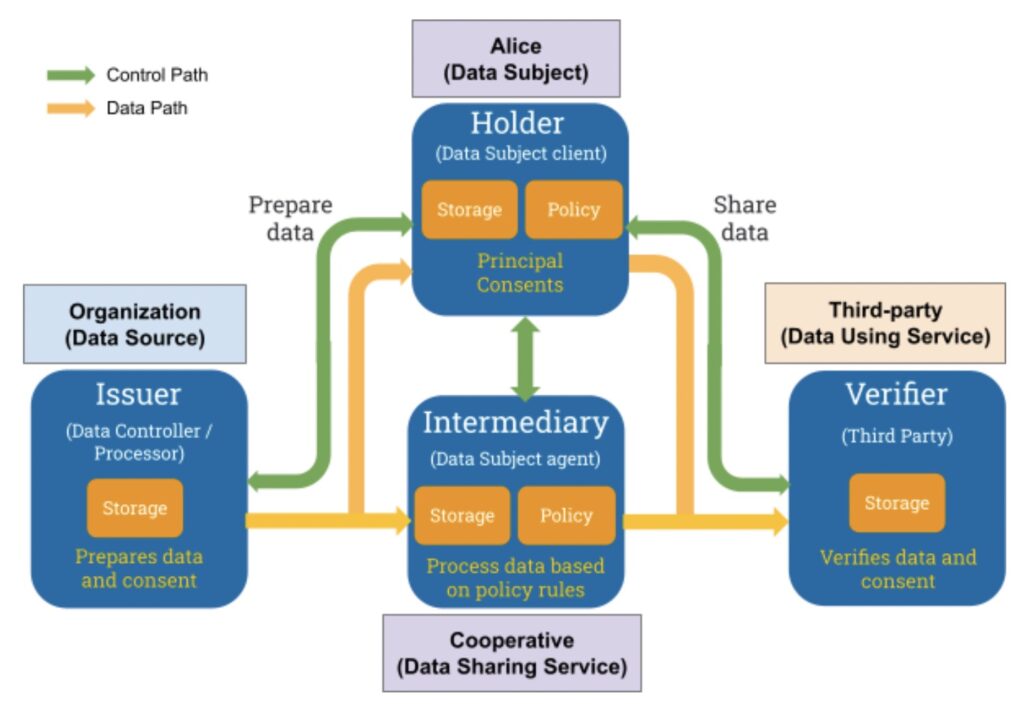
Two layers or paths when performing data exchange are described in the diagram.
- A data path (yellow arrows) composed of Verified Credentials (VCs) and interfaces to a data repository.
- A control path (green arrows) that sets the conditions for personal data usage, given through a data subject consenting to collecting, processing or sharing of personal data.
Each actor in the diagram has three different role types: a data role, a Distributed Ledger Technology (DLT) role, and a privacy role.
- The data role represents Data Subject who the collected data relates to, the Data Source that collects the data, the Data Sharing Service that processes the data prior to sharing the data, and Data Using Service which provides services based on the shared data.
- In addition to the standard DLT roles an additional role called Intermediary is introduced. As described before, the Intermediary facilitates the processing of data on behalf of the Data Subject prior to sharing with a third party.
- The privacy roles are the standard Data Controller/Processor, Data Subject, and Third-party. To better understand the Data Subject, it is split into two, a client and an agent. The Data Subject has direct control via the Client. The Agent allows the Data Subject to delegate control to the Agent (as a proxy).
The final aspect to understand are the key functions to enable the Intermediary to act on behalf of the Data Subject. The Intermediary requires a privacy function that applies the transformation and the privacy control selected by the Data Subject. For example the Data Subject may give consent to processing anonymized personal data that would be controlled by the privacy engine. The storage function may be in a wallet or a pseudonymized database with restricted access.
Summary
While it may look like most of the work in ToIP relate to VC’s, there is also the work from Inputs and Semantics work group that look at standardizing the storage, portability of the personal data, and creating a layered schema that helps with setting the policy engine when preparing and sharing of the data.
The Data Governance Act can be supported based on the technology being promoted in ToIP Working Groups. The work underway in ToIP Working Groups are aligned with the specific requirements of the Data Governance Act. Both ToIP and the DGA are avoiding a pervasive data ecosystem that promotes the surveillance economy. We both put a data exchange with humans at the center of any data transfer.
A future blog post will look at the Digital Markets Act in relation to ToIP. When an organization exceeds a threshold of users and net income, they are required to adhere to the rules of a Gateway stipulated by the Digital Markets Act. More in the next post.
References
- Promoting data sharing: presidency reaches deal with Parliament on Data Governance Act, November 30th 2021
https://www.consilium.europa.eu/en/press/press-releases/2021/11/30/promoting-data-sharing-presidency-reaches-deal-with-parliament-on-data-governance-act/ - HL7 FHIR
http://hl7.org/fhir/ - REGULATION OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL on European data governance (Data Governance Act), November 25th 2020
https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A52020PC0767 - MyData Operators
https://mydata.org/mydata-operators/ - Digital Governance Act proposes sharing data for the public good and selflessness – the concept of Data Altruism, January 28th 2021
https://eudatasharing.eu/news/digital-governance-act-proposes-sharing-data-public-good-and-selflessness-concept-data - The Digital Markets Act: ensuring fair and open digital markets
https://ec.europa.eu/info/strategy/priorities-2019-2024/europe-fit-digital-age/digital-markets-act-ensuring-fair-and-open-digital-markets_en
The Trust over IP (ToIP) Foundation announced a critical governing framework (PDF) to assist Santa in making his toughest choices during Christmas Eve.
For generations, Santa used many information sources, potentially unreliable, to choose gifts. However, with the advent of verifiable credential standards, systems, and governance, a more trustworthy ecosystem is being built which will issue NAUGHTY and NICE verifiable credentials based upon trustworthy evidence and accountability standards for all participants.

ToIP, working closely with the Santa-led Meaningful Gift Alliance (MEGA), applied its ground-breaking Metamodel Specification to define the ecosystem whereby trustworthy NAUGHTY and NICE credentials will be made available to Santa on Christmas Eve. This effort is expected to save Santa and his elves around 3.14159 million elf-hours per Christmas event which translates into a minimum of 742,000 additional toy deliveries for the 2.2 billion children of the world. #logistics #supplychain
Santa is thrilled. “Those NAUGHTY and NICE lists are just too difficult to scroll through when I’m out all-night delivering presents. I get acid reflux worrying that I’ll get my lists mixed up! This new ecosystem delivers all the information I need right to my satellite smartphone with the confidence I need to sail through the night!” #UXdesign

The Governance Framework (PDF) sets nuanced and contextual rules for the privacy protection of BAD and GOOD life events for children, used as input to the quantum-computer generated algorithm that issues NAUGHTY and NICE credentials. It also allows for parents, guardians, and child-advocates to petition on a child’s behalf. The Glossary of Terms for uses for the MEGA Governance Framework (PDF) is supported by a Trust Over IP terms community using the Trust Over IP terms wiki tool.
“While we want to save Santa some stress, the main focus is ensuring every child gets a meaningful gift each gift-giving season.” says Nichola Hickman, Secretariat for the Meaningful Gift Alliance. “We consulted with many meaningful gift-givers, including representatives for Wookie Life Day, Mother Earth, the IFFF (International Federation of Fairy Godmothers & Tooth Fairies) and the Free Magi-Sons. They all had experienced fraud from grown-ups claiming to be children, so we are delighted with this new method of ensuring that every child gets exactly what they deserve.”
Bids will be announced shortly for vendors for MEGA’s technical infrastructure.
MEGA also joined the Good Elf Pass Initiative whose “interoperability blueprint” supports its crucial role as issuers of these credentials. The ground-breaking “Hypersleigh” blockchain standard will also support rapid delivery and high security for all Meaningful Gifts. #hypersleigh
For more information on these emerging ecosystems and the Trust Over IP Foundation, contact us at https://trustoverip.org/contact/. Happy Holidays and Happy New Year!
Following the September announcement of its first tools for managing risk in digital trust ecosystems, today the ToIP Foundation announced three more pairs of tools to assist in the task of generating digital governance and trust assurance schemes:
- The ToIP Governance Framework Matrix and Companion Guide.
- The ToIP Trust Assurance and Certification Template and Companion Guide.
- The ToIP Trust Criteria Matrix Template and Companion Guide.
“These three new tools—each with its accompanying Companion Guide—are explicitly designed to simplify and streamline the process of developing robust governance for any digital trust community building on ToIP infrastructure,” said Scott Perry, co-chair of the ToIP Governance Stack Working Group (GSWG) and a certified WebTrust auditor. “They can help turn a job that often takes years into one that takes weeks or months.”
The physical credentials we use today, such as credit card and driver’s licenses, have governance frameworks and trust assurance schemes built by governments and industry associations over many years. Now we are moving to digital credentials verified using cryptography, we need to make the process of adapting these existing governance frameworks—or creating new ones explicitly tailored for digital life—much easier and faster.
“Governance is both simple and complex. Everyone has their own ideas of what Governance is and should be. The complexity comes when multiple parties need to agree on what it is and should be,” said Savita Farooqui, GSWG member and primary author of the Governance Framework Matrix. “The Governance Framework Matrix divides the problem in small chunks and provides a flexible framework to define governance and seek agreements.”

The Governance Framework Matrix is a recipe for setting the process of governance in motion. Without a starter set of governance topics to drive discussion and consensus, governing bodies stall in its formation.

The Trust Assurance Companion Guide explains in detail, in plain language, how accountability is generated from community participation in a governance framework.
“The Trust Assurance Template and Companion Guide is akin to the ‘Cliff Notes of Accountability’,” said Drummond Reed, GSWG co-chair. “When you combine it with the Trust Criteria Matrix, it means you don’t need to be a cybersecurity audit professional to grasp what is needed to meet the accountability requirements of your digital trust ecosystem.”
This statement was co-written by DIF and ToIP.
On 3rd August 2021, the World Wide Web Consortium proposed advancing the Decentralized Identifiers (DIDs) v1.0 specification to their W3C Recommendation stage, the ultimate level of the W3C standards process, which indicates that the specification as currently defined is technically sound, mature and ready for adoption. This includes the expectation that this will allow for widespread implementation, as well as further development and ongoing evaluation, paving the way for future versions.
Collectively, the memberships of the Decentralized Identity Foundation (DIF) and the Trust Over IP (ToIP) Foundation represent over 350 companies globally who are committed to the development and implementation of decentralized identity and trust infrastructure. Many of these organizations have contributed directly or indirectly to the W3C DID 1.0 specification for one simple reason: the DID layer of cryptographically verifiable identifiers is foundational to the common infrastructure we are building together and on top of; therefore, this spec is an integral part of DIF’s and ToIP’s shared vision for an empowered, secure and interoperable future, and in line with W3C TAG Ethical Web Principles.
As such, DIF and ToIP support the Decentralized Identifiers (DIDs) 1.0 specification becoming an official W3C Recommendation. DID 1.0 represents the efforts of over thirty active W3C Working Group contributors over the past two years— on top of contributions from dozens of others in the W3C Credentials Community Group and its predecessors for several years before that. This is a significant milestone in the digital identity sector. Having common ground for development, particularly in terms of interoperability, allows work to continue with renewed energy and focus. It also mitigates the risk of shifting goalposts, which seriously hinders long-term development, investment, and widespread adoption.
DIDs are a critical part of a technical foundation for the products and activities of many of our members. Many of the implementations in the DID Working Group’s implementation report were developed by engineers and companies who collaborate openly at DIF on points of technical interoperability, and at ToIP on points of policy and governance. DIF also hosts the Universal Resolver, a community project which puts practical intra-DID method interoperability into practice by co-developing a “translation engine” for diverse DIDs with contributions from DIF members and non-members alike. Similarly, other DIF efforts like the DID Communications protocol and the Presentation Exchange protocol and ToIP efforts like the ToIP Trust Registry Protocol serve to align a broad range of implementations and ecosystems already building on these standards, laying the groundwork for robust interoperability across ecosystems and diverse families of technologies.
This specification is the result of half a decade of sustained, broad-based, dedicated work on the part of W3C, DIF, and ToIP members. We acknowledge also the work done by numerous, forward-thinking organizations who have already built working implementations using the provisional specification, thereby laying the foundations of new infrastructures for “identity data”. We believe DIDs will change the course of digital identity by building in better user controls, portability and interoperability at the lowest possible level, while also offering increased security and simplicity for implementers and service providers. This advancement unlocks new opportunities for our digital lives, and we look forward to leveraging DIDs and other technologies developed in the community to champion a new class of user-first, self-owned digital identity systems.
Signed,
DIF & ToIP
October, 2021
We recently had the honor to host a presentation from our Canadian counterparts in Ontario about their technology roadmap for their Digital Identity (ID) program.
The aim of their program is to “make accessing online and in-person services simpler, safer and more secure”, and they’re aiming to introduce Digital ID later this year.
They’ve been busy since their announcement in October 2020, hosting roundtable discussions with large market participants, surveying and consulting with the public and small-to-medium businesses, developing a tech roadmap to get questions and input from private-sector partners, and publishing the technical tools they’re going to leverage.

The recent presentation to the ToIP Foundation was to further their goal of aligning and interoperating with the broader market for digital identity. They recognize the importance of market engagement, technology standards, and of partnering with the private sector in building a digital identity ecosystem. Ultimately, all this will help drive end user adoption and the delivery of value.
The presentation covered:
- A summary of findings from government-led public consultations on digital identity
- An overview of Ontario’s Digital ID technology roadmap, and discussions about the technology stacks and infrastructure
- Ontario’s proposed conceptual model for digital identity, and the principles that inform it
The presentation emphasized how the Government of Ontario’s digital identity strategy and roadmap is building upon the ToIP dual-stack model. It was exciting and gratifying to see a major public sector organization contributing to a digital identity ecosystem based on the interoperable open standards that are the heart of our efforts here at the ToIP Foundation. Equally, we hope that Ontario will benefit through exposure of their efforts to our worldwide presence—and further inspire others to adopt decentralized digital trust infrastructure.
If you are not yet a member of the Trust Over IP Foundation and wish to participate in future state-of-the-art member briefings such as this one, we encourage you to read more about membership.
The Internet is one of the most extraordinary developments in human history. It is connecting the world farther, faster, and deeper than any previous communications network. It is steadily digitizing every company, industry, and economy it touches. And it is establishing new pathways for information of all types to flow.
Unfortunately, all of this has come with a growing downside. The Internet wasn’t designed with an integrated layer for digital identity, security, and privacy. As a result, we are now suffering from cybersecurity and cyberprivacy problems so severe that they have at times brought entire companies and industries to their knees.
The Trust Over IP (ToIP) Foundation was launched in May 2020 to tackle this problem at its very core: to define a complete architecture for Internet-scale digital trust. It combines cryptographic assurance at the machine layers and human accountability at the business, legal, and social layers. While ambitious, this mission is so urgent and essential that the Foundation has grown from its initial 27 founding member organizations to over ten times that number in just one year.
As part of the Foundation’s launch, working groups were established from the dedicated efforts of our founding members and volunteers. What those groups have accomplished in their first year has been phenomenal. Specifications, recommendations, guides, white papers, and glossaries have all been delivered. Through the groups’ efforts the Foundation has supported Digital Trust advances in many organizations and operations, especially important as the world grapples with the pandemic and the voluminous increase in everyday online activity.
Here’s a small taste of what our working groups have been up to since their inception last year.
Technology Stack Working Group (TSWG)
The TSWG provides guidance and specifications that support the ToIP 4-layer model from a technical standpoint.
The TSWG has, amongst many accomplishments:
- Created and pushed a Task Force recommendation that constructs a mapping of Kim Cameron’s “Laws of Identity”
- Created a task force in late 2020 to create early specifications for Authentic Chained Data Containers. This task force is focused on the semantics of source provenance, authorization provenance, and delegation.
- Focused the Interoperability Task Force on the creation of interoperability test suites that leverage and extend the Hyperledger Aries test suites. Multiple underlying Layer-1 technologies are being examined as well.
- Focused the Technical Architecture Task Force on building the TSS (ToIP Standard Specification) that defines the overall technical requirements for the four layers of the ToIP Stack
- Created a Trust Registry Task Force to handle creation of the specifications and API (OpenAPI 3.0 compatible) for trust registries. This work was spawned from the urgent need identified by the Good Health Pass Interoperability Working Group.
Governance Stack Working Group (GSWG)
The GSWG specifies tools, templates, and other resources for developing governance frameworks (collections of rules and policies). These, in turn, support the integration of the legal, business, and social components of Digital Trust.
The GSWG has, amongst many accomplishments:
- Made steady progress with the ToIP Governance Architecture TSS
- Advanced the ToIP Governance Metamodel to the point where the GSWB now plans to issue it as a separate specification (apart from the ToIP Governance Architecture TSS), along with an associated Companion Guide
- Contributed heavily to the governance framework recommendations in the Good Health Pass Interoperability Blueprint
- Advised the authors of several ToIP-based governance framework projects in the market
- Initiated a Trust Assurance Task Force focusing on governance risk assessment and accountability
- Drafted a Risk Assessment Worksheet Template and associated Companion Guide
Ecosystem Foundry Working Group (EFWG)
The EFWG facilitates a community of practice among governance authorities, implementers, operators, and service providers of Trust over IP Layer-4 ecosystems.
The EFWG has, amongst many accomplishments:
- Formed the Internet of Research Ecosystem Task Force to pioneer implementation of academic resource identifiers ecosystems for the research community
- Created the COVID-19 Credentials Governance Framework Task Force to develop reference materials, best practices, and templates that enable diverse organizations to respond with technology
- Formed the YOMA Ecosystem Task Force to create a ToIP-based Governance Framework to positively impact youth and local communities around the world
- Formed the Human Trafficking Safety Response Task Force to research the use of ToIP models to effect the transformation of global human trafficking response
- Drafted the initial Ecosystem Foundry Concepts and Workflow Model to aid ecosystem development and operation
Utility Foundry Working Group (UFWG)
As with the EFWG, the UFWG also facilitates a community of practice among governance authorities, implementers, operators, and service providers, but instead for Trust over IP Layer-1 utilities.
The UFWG has, amongst many accomplishments:
- Worked alongside utility conveners to document their utility into story formats
- Committed best practice documents to the WG GitHub Repository, such as Decentralized Network Best Practices and Decentralized Network Design Principles
- Worked to publish a public UFWG paper with which will incorporate many of our outputs as well as case studies from utility projects we’ve interfaced with
- Committed to expanding the coverage of the UFWG to non-Indy-based ledgers.
Inputs and Semantics Working Group (ISWG)
The ISWG provides an open forum for discussing the concepts and components that will ultimately shape a Dynamic Data Economy (DDE), a safe and secure decentralized data sharing economy.
The ISWG has, amongst many accomplishments:
- Delivered whitepapers such as Decentralized Resource Identifiers in the Research Landscape
- Contributed to the Good Health Interoperability Blueprint (“GHP Blueprint”), such as for “Standard Data Models and Elements” and “Security, Privacy, and Data Protection”
- Housed the Health Care Task Force (HCTF) that led to GHP Blueprint recommendations
- Defined a privacy controller credential to ensure trustworthiness for the use of decentralized identifiers across ecosystems
- Facilitated several presentations from external presenters of storage and portability solutions
- Tackled important security concepts such as data correlation attacks, machine-readable data agreements, and data protection requirements
Concepts and Terminology Working Group (CTWG)
The CTWG analyzes and maintains terminology requirements of stakeholder groups within and outside the ToIP Foundation.
The CTWG has, amongst many accomplishments:
- Maintained glossaries for the reuse of terms across groups, with mapping of terms and definitions across groups to encourage harmonization
- Surveyed the available terminology development and maintenance tools on the market
- Authored its own specification for a ToIP Term tool
- Innovated with an approach called “terms wikis” to enable different stakeholder groups to develop and maintain glossaries in their own contexts.
Interoperability Working Group for Good Health Pass (IWG-GHP)
The IWG-GHP facilitated a community of practice among implementers, issuers, holders, verifiers, governance authorities, and other participants within the Good Health Pass digital trust ecosystem.
The IWG-GHP has, amongst many accomplishments:
- Authored a blueprint based on an outline created by ID2020, going live in June 2021
- Coordinated the meeting and responses of ten different drafting groups
- Completed a 150-page report, the Good Health Pass Interoperability Blueprint, that makes key recommendations on how to reopen global travel with verifiable credentials for sharing COVID-19 health status (tests, vaccinations, and recovery).
There’s More To Do
Our work is just getting started! We encourage anyone interested in Digital Trust to join Trust Over IP and get involved in our working groups.
Read more about membership and find out the latest working group activity.
Here’s to our continued advancements and successes!
The growing interest in verifiable digital credentials, such as mobile driver’s licenses or digital health passes, means companies and governments need new tools for managing risk in this decentralized infrastructure. “Risk management in financial services, such as banking and credit card networks, is a mature field,” said Scott Perry, co-chair of the ToIP Foundation Governance Stack Working Group. “But as we move into decentralized identity management, where individuals manage credentials in their own digital wallets, we need new risk management tools designed for this paradigm.”
To begin to fill this gap, today the Trust Over IP (ToIP) Foundation announced the release of the ToIP Risk Assessment Worksheet (Excel format) and Companion Guide (PDF). These new tools are intended to equip architects of digital governance frameworks — ”rulebooks” for establishing trust online—with the knowledge they need to perform a risk assessment grounded in generally accepted global standards and techniques, including:
- Proper consideration and identification of potential risks,
- Critical analysis of risks in terms of likelihood and severity,
- Calculating a systematic risk impact score,
- Triaging risks for further treatment,
- Risk mitigation requirements and strategies,
- Performance of an annual review to reassess existing risks and consider new ones.
The Risk Assessment Worksheet and Companion Guide provides a step-by-step method of performing a systematic risk assessment that conforms with industry-standard guidance such as ISO/IEC 27005 and NIST 800-30. This process identifies and categorizes risks by likelihood and severity in order to create a risk score that can be color-coded, and stack ranked to highlight the need for countermeasures as shown below. The Worksheet and Companion Guide include enough background and educational content that even risk assessment novices should be able to drive the risk assessment process. “A key missing piece of building open digital trust ecosystems has been a deep understanding of the various risks they introduce.
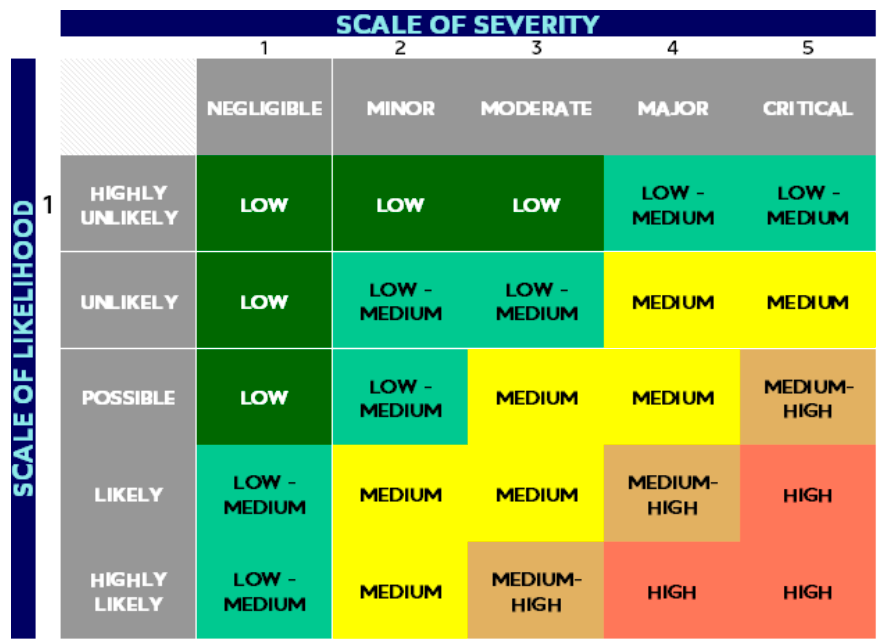
This can scare off key stakeholders“, said Darrell O’Donnell, CEO of Continuum Loop and Chair of the ToIP Governance Stack Working Group. “The Risk Assessment Worksheet is a powerful tool that helps create clarity about where the real risks are in an ecosystem and what to do about them.”
The Risk Assessment Worksheet and Companion Guide are the first deliverables from the ToIP Governance Stack Working Group (GSWG), whose mission is to produce a complete suite of tools, models, templates, and guides for digital governance frameworks. GSWG member Vikas Malhotra, CEO of WOPLLI Technologies, explained why risk assessment was at the top of the list: “Willingness to take risks is key to forming trust. A risk assessment process helps to qualify and quanfy the risk in a situation, so that the potential trustor can use the information to understand if they should take the risk or not.”
These new tools for risk assessment are already being put to use by digital trust ecosystems being incubated within the ToIP Ecosystem Foundry Working Group. An example is the YOMA governance framework for youth education and life skills credentials in Africa. “Designing a digital trust ecosystem without first assessing the specific risks it is intended to address is like laying underground pipes without testing them to determine the possibility of leakages” said Frednand Furia, who is leading the Yoma Trust Assurance Task Force. “The ToIP Risk Assessment Worksheet and Companion Guide have already proved to be very effective in architecting the YOMA Rules governance and trust framework.”
Digital health passes — often mischaracterized as “vaccine passports” in the popular press — are making headlines as a key component in the drive to restore global travel and restart the global economy after the massive impact of the COVID-19 pandemic.
Enabling individuals to receive and selectively share proof-of-test, proof-of-vaccination, and proof-of-recovery with the highest standards for security, privacy and data protection will allow destination countries and travel systems worldwide to accept credentials from multiple market vendors. But concerns related to equity and access can only be addressed if these health pass implementations are designed to be interoperable.
As the leading global consortium for interoperable digital trust infrastructure, the ToIP Foundation has partnered with the Good Health Pass Collaborative – a project of ID2020 – to host a new Working Group focused on the core issues of interoperability, privacy, and equity for digital health passes. The Interoperability Working Group for Good Health Pass consists of nine drafting groups, each focused on a specific interoperability challenge as defined in the Interoperability Blueprint Outline.
“The Good Health Pass Collaborative is bringing people together to solve a set of problems that affect the entire world,” said John Jordan, executive director of the ToIP Foundation. “This ambitious effort uniquely aligns with the mission of ToIP because it requires interoperable digital credentials that can be accepted and verified anywhere they are needed. Getting this right, and doing so now, will not only make it safe for people to travel again, it will open the door for new tools and services that can solve other challenging problems that also require global-scale digital trust. For these reasons, ToIP is honored to contribute to this urgent global mission by hosting the Interoperability Working Group on behalf of the Good Health Pass Collaborative.”
Each drafting group, consisting of volunteer representatives from around the world representing the health, travel, technology, and policy sectors, will first conduct an intensive 30-day sprint to develop an initial set of draft recommendations. This will be followed by a second 30 day community and public review process to develop a final set of recommendations.
“Digital health passes – If properly designed and implemented – could offer a path to safely restore domestic and international travel, resume certain aspects of public life, and restart the global economy,“ said ID2020 executive director, Dakota Gruener. “Collaboration is critical at this juncture. Our organizations share a commitment to ensuring that digital health passes are designed and implemented in ways that serve the needs of the individuals and institutions that rely on them, while simultaneously protecting core values like privacy, civil liberties, and equity. ToIP has developed a powerful set of tools and models for digital trust frameworks, and we are delighted to be partnering with them in this critically important effort.”
The nine drafting groups collaborating within the new Working Group are:
- Paper Based Credentials will define how a paper-based alternative can be created for any digital health pass so access will be available to all.
- Consistent User Experience will specify the common elements required so that individuals can easily, intuitively, and safely use digital health pass implementations.
- Standard Data Models and Elements will determine the core data items needed across all digital health pass implementations for both COVID-19 testing and vaccinations.
- Credential Formats, Signatures, and Exchange Protocols will specify the requirements for technical interoperability of Good Health Pass implementations.
- Security, Privacy, and Data Protection will define the safety requirements for Good Health Pass compliant implementations.
- Trust Registries will specify how verifiers can confirm that a digital health pass has been issued by an authorized issuer.
- Rules Engines will define how digital health pass apps can access different sources of policy information to determine what test or vaccination status is needed for a specific usage scenario.
- Identity Binding will specify the options for verifying that the holder of a digital health pass is the individual who received the test or vaccination credential.
- Governance Framework will define the overall set of policies that must be followed for an implementation to qualify as Good Health Pass compliant.
By adhering to the Good Health Pass Interoperability Blueprint that will be synthesized from the outputs of these nine drafting groups, airlines, airports, hospitality industries, international customs officials and others will be able to process visitors easily without requiring additional unnecessary steps mandated by proprietary systems. Travelers will not be confused about which credential they need for each point of verification. Moreover, since individuals will be fully in control of their own personal data in credentials in their own wallets or devices, they can be confident that their private health data is not being tracked or misused.
Interested organizations are invited to join the ToIP Foundation to participate directly in this new Working Group or in the public comment period in May. They are also encouraged to join the Good Health Pass Collaborative at ID2020 to participate in the construction, adoption, and advocacy of the Good Health Pass Interoperability Blueprint.
When the ToIP Foundation launched in May 2020, our mission was to define a new model for achieving trust online—a model that breaks away from the thousands of siloed solutions for secure, privacy-enhancing digital identity and trust that do not work with each other. This lack of interoperability costs billions of dollars per year in complicated and time-consuming integration and hinders adoption by the very customers we are trying to serve.
Our goal is to drive adoption of a new model for digital trust based on open standard digital wallets and digital credentials that are every bit as interoperable as the physical wallets and paper or plastic credentials that we use every day—to do everything from getting on a plane to entering a hospital to signing a mortgage. As these new tools emerge as the primary mechanism for contactless identity verification, payments, and other online transactions, they will become as essential to our digital lives as browsers and email clients have become to the Web today.
As that happens, it is critical to avoid recreating the vendor-lock in and fragmentation of the “browser wars” that hindered the early days of the Web. Interoperable solutions that avoid vendor lock-in are paramount for a vibrant digital marketplace where consumers are free to choose their preferred digital wallet software from a variety of vendors and use digital credentials from any issuer as they choose.
The need for market-driven interoperability
Open standards alone do not produce interoperable market solutions—there are too many ways interoperability can still go off the rails. Testing labs are another step in the right direction—but vendors need incentives to use them, and those incentives can be scarce in a new market.
The ToIP Foundation recognized that, as our economy grows increasingly digital and collaboration tools grow steadily more powerful, there is a new path to interoperability: tapping market dynamics to drive incubation and adoption of truly interoperable solutions.
With this approach, vendors and customers voluntarily work together to develop interoperability testing requirements designed to meet explicit customer needs in the market. Vendors then satisfy those requirements by passing these interoperability tests with production-ready software.
Introducing the ToIP Interoperability Profile (TIP)
To facilitate this new approach to market-driven interoperability, the Technology Stack Working Group of the ToIP Foundation developed the ToIP Interoperability Profile (TIP). A TIP represents a specific combination of technologies that span each of the four layers of the ToIP technology stack in order to meet the requirements of a set of target customers in one or more digital trust ecosystems.
TIPs can be designed, refined and supported by multiple vendors and customers wishing to collaborate on interoperability. A TIP typically includes the following elements critical to customer success:
- Use cases capturing the specific requirements of customers in one or more digital trust ecosystems.
- Design principles that must be clearly defined when combining technology and business policies to formulate a solution architecture.
- Documentation that clearly communicates the design, architecture, features, and benefits of a TIP to the digital trust ecosystems targeted for adoption.
- Best practices and implementation guidance for adoption of a TIP, including how to incorporate policies from the ToIP governance stack.
- Interoperability tests that enable vendors supporting the TIP to be certified for verifiable interoperability.
- Adoption metrics and case study references that provide quantifiable evidence of the real market impact.
TIPs harness market forces to drive convergence on interoperability
Each TIP consists of two types of components:
- Fully-standardized components of the ToIP stack. These components, called ToIP Standard Specifications (TSS), are standards that have already gained Foundation-wide approval.
- Custom components that are specific to a TIP. Some places in the ToIP stack do not yet have agreed-upon specifications. For these gaps, a TIP must specify how it fills the gap via an open community specification that can be implemented by any vendor or open source project.
A conceptual “lego block” picture of a complete four-layer TIP—showing how it is constructed from a combination of standard TSS components and custom TIP-specific components—is shown in the figure below.

Launching the Saturn-V TIP
The first TIP published by the ToIP Technology Stack Working Group is named for the historically significant multi-stage rocket platform, the Saturn-V. This TIP emerged from work begun at a 2019 Connect-a-Thon event held by the Hyperledger Indy community. When the ToIP Foundation was launched in May 2020, ToIP members including Commerzbank (Main-Incubator), esatus AG, Evernym, IBM, Trinsic and idRamp recognized the opportunity to coalesce their collaboration into a TIP.
Once the ToIP Technology Stack Working Group was formed, it established the criteria for managing the lifecycle of TIP from incubation through design, demonstration, acceptance and adoption. The Saturn-V collaborators then proposed their TIP following this process and it was formally accepted as a Draft Deliverable by the Technology Stack Working Group at their 24 August 2020 meeting.
The next stage: mission-critical collaboration on interoperability testing
All the vendors participating in the Saturn-V TIP actively pair with developers from other participants to work through agreed-upon test plans. Having the Technology Stack Working Group oversee the TIP development life cycle on behalf of all participating vendors ensures a more transparent and robust joint testing project than a typical multi-vendor “plug-fest”.
Since the technologies used for the Saturn-V TIP are Hyperledger Indy and Hyperledger Aries at layers 1-3 of the ToIP Technology Stack, the open source Aries Test suites will be used as the baseline for all test plans. Participating vendors are currently tackling the following stages of the Saturn-V Interop Test Plan One:
- Self-Validation against Aries Protocol Test Suite for Aries Interop Profile v. 1.0
- Peer-Validation
- Core Aries Interop Profile v. 1.0 (Aries RFC 302), which supports DID connections, issuing credentials, and fulfilling proofs
- Connectionless Proofs using the Service Decorator (Aries RFC 56),
- HTTP over DIDComm (Aries RFC 348).
Future missions
Once Test Plan One is complete, TIP Participants will define Saturn-V Interop Test Plan Two which intends to minimally include peer-to-peer validation for:
- Core Aries Interop Profile v. 2.0 (content and scope not yet defined by community)
- Out-of-Band Protocol (Aries RFC 434)
- End-to-End testing the Aries Agent Test Harness (contributed by the Government of British Columbia)
Once these stages of interoperability testing are completed, the Technology Stack Working Group will be able to assess whether component specifications of this TIP meets the criteria to become a TSS. If so, these will be advanced to become their own Draft Deliverables for ultimate approval by the Working Group and then the ToIP Steering Committee.
Please join us
We invite you to join in development of the Saturn-V TIP and formulation of new TIPs that provide full-stack interoperability for digital trust ecosystems. If you are not yet a member of the ToIP Foundation, membership is open to anyone—individual or organization—at both free and paid membership levels. For more information, please visit the Foundation membership page.
TIP development is coordinated through the ToIP Technology Stack Working Group.
To join the Technology Stack Working Group, go to https://lists.trustoverip.org/, log in with the email address of your ToIP Foundation membership, then subscribe to the mailing list.
