When it was launched in May 2020, the ToIP Foundation summarized its mission in a single 20-page white paper called “Introduction to Trust Over IP”. This paper was based on an article called The Trust Over IP Stack published in the December 2019 special issue of IEEE Communications Standards Magazine called The Dawn of the Internet Identity Layer and the Role of Decentralized Identity.
Two years later, with ten times more members and double the original number of working groups, the Foundation is a much more mature organization. Despite this growth, we are very pleased that the original vision of the ToIP stack has stood the test of time.
In summer of 2021, we put out a call to all ToIP members to participate in a series of “community writing workshops” to collaboratively produce two new Foundation-wide deliverables:
- Introduction to ToIP V2.0 (PDF)
This is the second-generation version of our original introductory white paper that would go more deeply into the origin and purpose of the ToIP stack and how it addresses the key challenges of decentralized digital trust infrastructure. - Design Principles for the ToIP Stack V1.0 (PDF)
This is an articulation of the key design principles we must follow in the design and development of all aspects of the ToIP stack.
We were thrilled that over two dozen members took us up on this challenge to participate over four months to produce these two documents, both of which have just been approved by the ToIP Steering Committee.
Introduction to ToIP V2.0
Our primary goal with this second-generation white paper was to make the vision and mission of ToIP accessible to a general audience—literally anyone who cares about the future of the Internet and how we can deal with the myriad security, privacy, data protection, and data sovereignty issues that have emerged as “the world’s greatest information utility” passes its first half-century of growth.
Our second goal was a “plain English” explanation of the overall structure of the four-layer, two-half sided ToIP stack using new graphics based on the wonderful interactive version developed by Peter Stoyko of Elanica. Here is the new static version of the diagram:
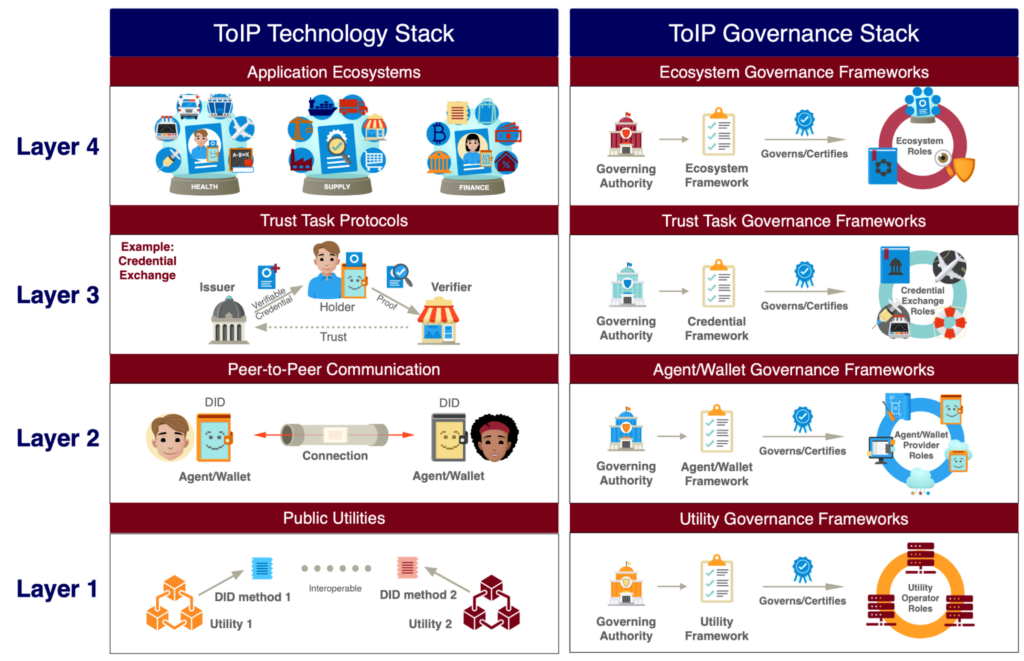
Our third goal was to provide a more complete introduction to the ToIP Foundation as a collaborative organization devoted to the design, development, adoption, and promotion of the ToIP stack—a guide to helping prospective members understand how and why to engage.
The resulting document is divided into the following sections:
- ToIP in a Nutshell
- Why Has Digital Trust Become Such a Major Problem?
- The ToIP Model for Digital Trust
- Applying This Model to the Digital World
- The ToIP Stack
- The ToIP Foundation
- How to Engage with the ToIP Foundation
- The Road Ahead
It is available as a PDF document here and on the homepage of the ToIP Foundation website.
Design Principles for the ToIP Stack V1.0
To establish a truly interoperable decentralized digital trust layer for the Internet as a whole, meticulous attention must be paid to the design of the ToIP stack. Given the tremendous growth of the ToIP Foundation—from 27 original founding member organizations to over ten times as many today—it was critical to form a strong consensus among the new members about the principles governing this design.
Another key reason to establish design principles for the development of a system is summarized in this quote from the start of the document:
The goal of any design principle is to provide guidance to the designers of a product, service, or system so they can take advantage of lessons learned from the success or failure of previous designs. Design principles represent accumulated wisdom that falls in between the generality of scientific laws and the specialization of best practices.
When it comes to a layered architecture for both technology and governance of decentralized digital trust infrastructure, the “lessons learned from the success or failure of previous designs” is prodigious. Thus the writing workshops for this document continued for four months in order to bring all the relevant design principles together.
To organize the final set of 17 principles into a logical progression, we followed a rubric suggested by co-editor Victor Syntez based on a 2006 blog post by cryptography pioneer Nick Szabo. Szabo distinguished between two types of “code”:
- Code written in a computer language expected to be executed by a machine (“dry code”), and
- Code written in a human language, i.e., laws, regulations, rules, policies and other forms of governance expected to be followed by humans (“wet code”).
Accordingly, we divided the principles into three categories:
- Principles of computer network architecture—these “dry code” principles represent fundamental lessons learned about the design of large-scale computer networked systems, especially the Internet:
#1: The End-to-End Principle
#2: Connectivity Is Its Own Reward
#3: The Hourglass Model
#4: Decentralization by Design and Default
#5: Cryptographic Verifiability
#6: Confidentiality by Design and Default
#7: Keys at the Edge
- Principles of human network architecture—these “wet code” principles represent fundamental truths about how trust relationships operate between humans—either individually or in groups:
#8: Trust is Human
#9: Trust is Relational
#10: Trust is Directional
#11: Trust is Contextual
#12: Trust has Limits
#13: Trust can be Transitive
#14: Trust and Technology have a Reciprocal Relationship
- Overall design principles—these three remaining principles apply to the overall design of the ToIP stack, “wet or dry”:
#15: Design for Ethical Values
#16: Design for Simplicity
#17: Design for Constant Change
Care was taken to not only explain each principle in plain English, but to analyze how it applies to the design of the ToIP stack at each layer. We summarized those recommendations using this table format:
| Layer | Relevance | Explanation |
| The ecosystem symbol represents the purpose of Layer 4 to support the applications needed to develop and sustain entire digital trust ecosystems. | ||
| The triangle symbol represents the Layer 3 verifiable credential “trust triangle” of issuer, holder, and verifier that enables parties using the ToIP stack to establish transitive trust. | ||
| The symbol of two connected mobile phones represents the purpose of Layer 2 as a universal peer-to-peer secure privacy-routing DID-to-DID communications protocol. | ||
| The anchor symbol represents the purpose of Layer 1 public key utilities to provide strong anchors for Decentralized Identifiers (DIDs) and their associated public keys. |
For each principle, in the “Relevance” column we assigned star ratings for each layer as follows:
| ★★★★★ | Highly relevant to the design of this layer |
| ★★★★ | Very relevant to the design of this layer |
| ★★★ | Moderately relevant to the design of this layer |
| ★★ | Somewhat relevant to the design of this layer |
| ★ | Only slightly relevant to the design of this layer |
Once all 17 principles had been compiled into a document with this format, the contributors felt that we had identified the “center of gravity” of the design of the ToIP stack that could now guide our work in completing it.
We strongly recommend this document for anyone who wants to deeply understand the rationale for our work at the ToIP Foundation. It is available as a PDF document here and on the homepage of the ToIP Foundation website.
Acknowledgments
Our thanks to Victor Syntez and Drummond Reed for serving as co-editors for these two documents and to the following ToIP members who contributed their time and expertise:
| Introduction to ToIP V2.0 | Design Principles for the ToIP Stack 1.0 |
| Carly Huitema Daniel Bachenheimer — Accenture Darrell O’Donnell — Continuum Loop Jacques Bikoundou Judith Fleenor — Trust Over IP Foundation Kaliya Young — COVID-19 Credential Initiative Karen Hand — Precision Strategic Solutions Karl Kneis — IdRamp John Jordan — Province of British Columbia Lynn Bendixsen — Indicio P. A. Subrahmanyam — CyberKnowledge Sankarshan Mukhopadhyay — Dhiway Networks Scott Perry — Scott S. Perry CPA, PLLC Vikas Malhotra — WOPLLI Technologies Wenjing Chu — Futurewei | Antti Kettunen Daniel Bachenheimer — Accenture Daniel Hardman — SICPA Darrell O’Donnell — Continuum Loop Jacques Bikoundou Jo Spencer — 460degrees John Jordan — Province of British Columbia Jonathan Rayback — Evernym Judith Fleenor — Trust Over IP Foundation Lynn Bendixsen — Indicio Mary Lacity — University of Arkansas Michel PlanteNeil Thomson — QueryVision P. A. Subrahmanyam — CyberKnowledge Rieks Joosten — TNO Sankarshan Mukhopadhyay — Dhiway Networks Scott Perry — Scott S. Perry CPA, PLLC Steven McCown — Anonyome Labs Thomas Cox Vikas Malhotra — WOPLLI Technologies Vinod Panicker — Wipro Ltd Wenjing Chu — Futurewei |
