The mission of the Trust over IP (ToIP) Foundation is to define an overall architecture for Internet-scale digital trust that combines cryptographic assurance at the machine layers (technology) with human accountability at the business, legal, and social layers (governance). Together these two halves form a complete four-layer architecture for decentralized digital trust infrastructure known as the ToIP stack as shown in this conceptual diagram:
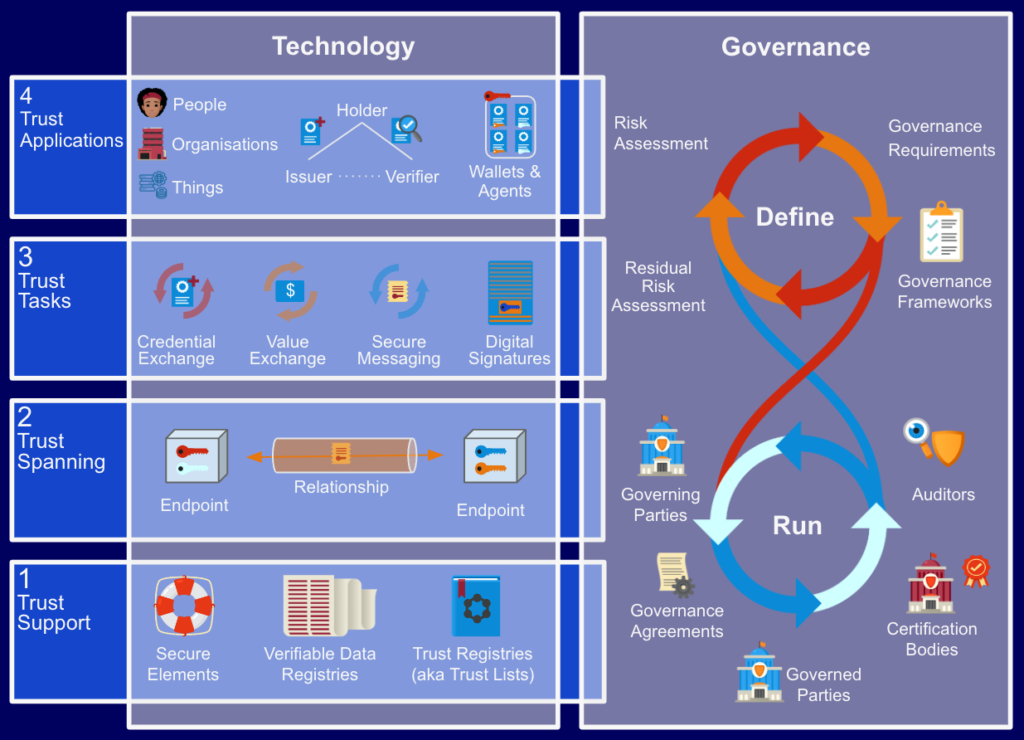 When the ToIP Foundation was launched in May 2020, the original 27 founding organizations knew the job of fully defining both sides of the ToIP stack would be a multi-year process involving hundreds of contributors and thousands of person-hours. Now, over four years later, we are well down that path. This page explains the original roadmap and shows where we are as of September 2024.
When the ToIP Foundation was launched in May 2020, the original 27 founding organizations knew the job of fully defining both sides of the ToIP stack would be a multi-year process involving hundreds of contributors and thousands of person-hours. Now, over four years later, we are well down that path. This page explains the original roadmap and shows where we are as of September 2024.
Stages of Development
The founding members recognized that the development process would need to proceed through four stages, each dependent on the one before it, as shown in this diagram:
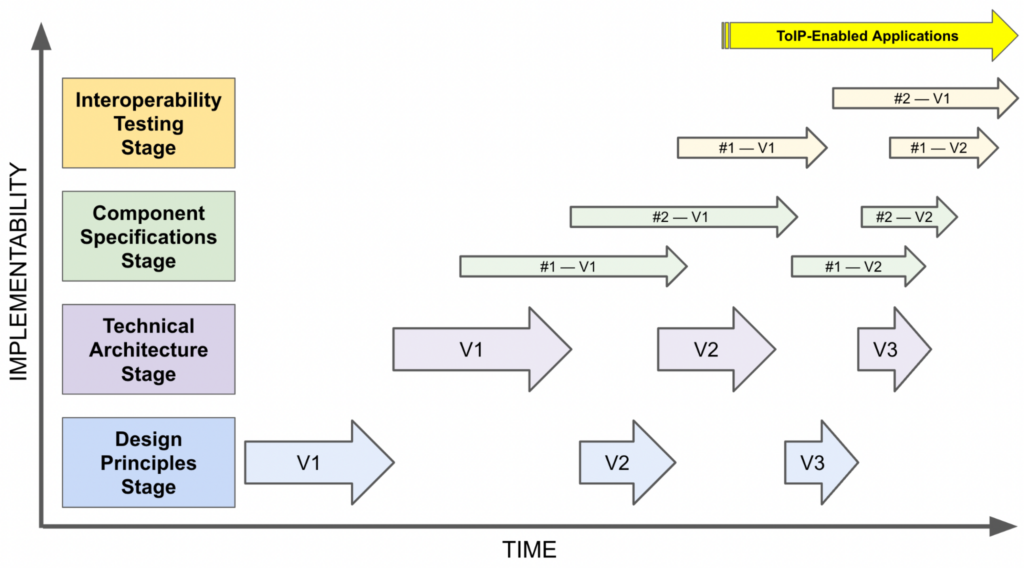
- Design Principles: The first stage was reaching agreement on the overall design principles for the ToIP stack as a whole. This process, which involved contributions from all ToIP Working Groups, resulted in the Design Principles for the ToIP Stack V1.0, which was approved by the ToIP Steering Committee on 11 November 2021.
- Technical Architecture: The second stage was to apply the design principles to the original conception of the ToIP stack to develop a complete set of layer-by-layer architectural requirements. This culminated in the publication of the first public review draft of the ToIP Technology Architecture Specification V1.0 on 14 November 2022. The second public review draft is scheduled to be published in September 2024.
- Component Specifications: These are the specifications required to fully implement the Technical Architecture requirements. The vast majority of these specifications are expected from other standards organizations (e.g., W3C Decentralized Identifiers (DIDs) 1.0, W3C Verifiable Credentials Data Model 1.1, ISO mDL, DIF DIDComm V2). The ToIP Foundation only intends to define new component specifications where there is a gap no other SDO is filling.
- Interoperability Testing: The final stage in enabling fully interoperable ToIP applications is the development of vendor-independent interoperability profiles, test suites, and certificate frameworks that can demonstrate conformance to all necessary component specifications.
Where Are We Now?
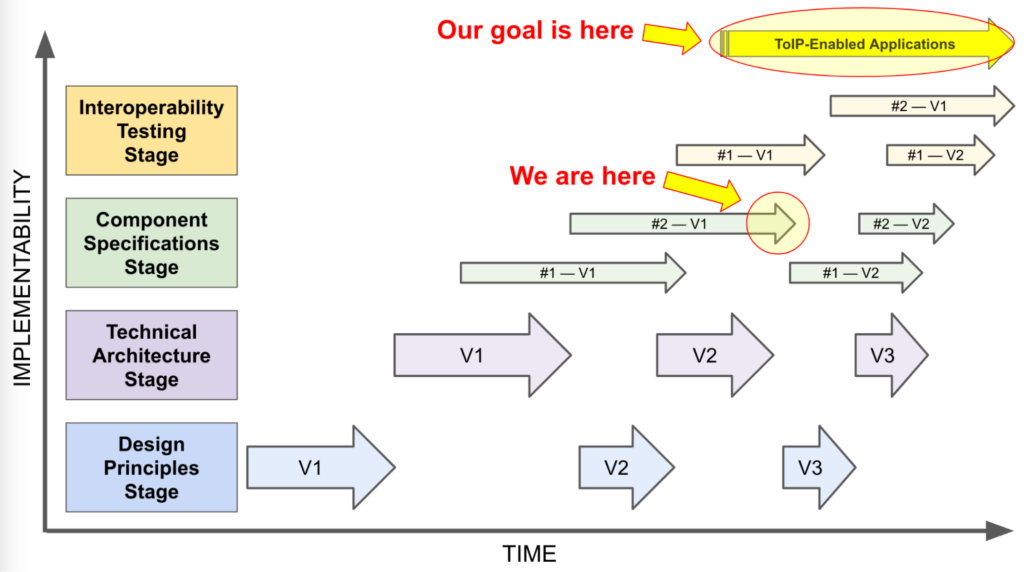
After the ToIP Technology Architecture Specification was published in late 2022, two of the most critical component specifications were not being pursued in any other standards body. So the ToIP Technology Stack Working Group started the following two task forces:
- The Trust Spanning Protocol Task Force had the job of defining the single Layer 2 protocol that serves as the keystone of the ToIP stack: the Trust Spanning Protocol. This work culminated in the first Implementers Draft being published in April 2024.
- The Trust Registry Task Force was chartered to develop a standard Layer 3 protocol for querying any trust registry (aka trust list) to answer questions like whether an issuer is authorized to issue a specific type of credential under a specific governance framework or a verifier is authorized to request a presentation of that type of credential. This too resulted in an Implementers Draft published in April 2024.
With these two component specifications ready — and learnings from both fed back into a second public review draft of the ToIP Technology Architecture Specification to be released shortly, the following diagram shows where we are as of September 2024:
 Where Do Other Technologies Fit Into The ToIP Technology Stack?
Where Do Other Technologies Fit Into The ToIP Technology Stack?
We are often asked, “Where does [name of existing technology/specification] fit into the ToIP stack?” Here are answers for some of the best-known technologies in this space:
- W3C Decentralized Identifiers (DIDs) are a ToIP Layer 1 supporting technology — in fact one would argue THE key supporting technology that enables the entire rest of the ToIP stack.
- Digital credential exchange protocols such as OID4VC*, DIDComm/Aries, ISO, and KERI are all ToIP Layer 3 trust task protocols (though not designed yet to run on top of the Trust Spanning Protocol).
- Digital credential format specifications such as W3C Verifiable Credentials Data Model, ISO mDL / mDOC, IETF SD-JWT, and ToIP ACDC are all cryptographic data formats designed to be exchanged with the Layer 3 credential exchange trust task protocols.
- tbDEX and other cryptographic value exchange protocols are also Layer 3 trust task protocols that can be integrated with the ToIP stack to take advantage of the security, metadata privacy, and interoperability features of the Trust Spanning Protocol.
Digital signature standards such as those from the Cloud Signature Alliance are also an ideal example of Layer 3 trust tasks that the ToIP stack will make much easier to integrate alongside other trust tasks.
Future Updates & Call to Action
As the build out of the ToIP stack continues, please check back with this page and watch the ToIP blog for updates. If you wish to become directly involved in any of the existing Task Forces of the ToIP Technology Stack Working Group — or propose a new task force (for example, for a new trust task protocol)—we invite you to become a member of the ToIP Foundation.
