Two weeks ago was the first full-scale Identiverse since the pandemic began, and host Ping Identity pulled out all the stops. It started off with a wonderful video splash with spotlighted drummers banging away, setting the stage for three days of wonderful entertainment, great keynotes, engaging sessions, and nonstop networking.
Ping CEO Andre Durand ‘s opening keynote set the tone by putting decentralized identity front and center. Stating that our current systems do not scale, Andre took us on a journey through the history of Identity solutions from passwords, to single sign-on, to OAuth, to centralized and federated identity.
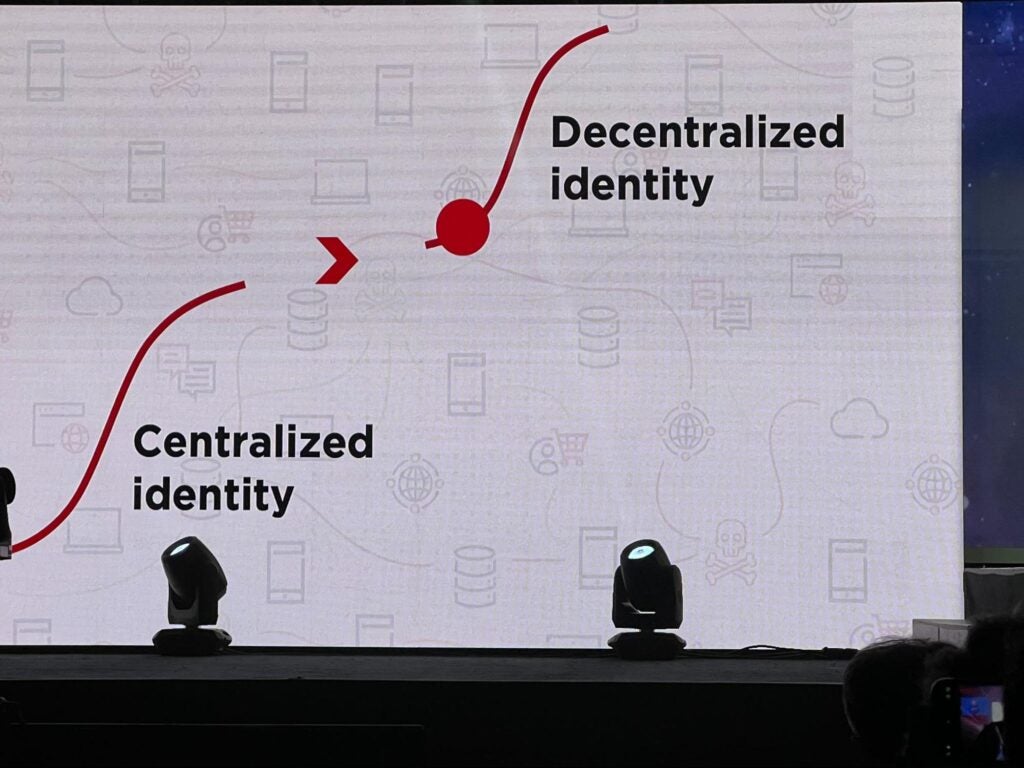
He then ended with what we all know at the Trust Over IP Foundation: that the future is decentralized identity.
It was not just a wonderful start to the conference, but a great summary of exactly why ToIP was founded: we are collaborating to develop the recommendations, standards, guides, and templates needed to connect the gap shown on Andre’s slide above.
If there was a real surprise at this year’s Identiverse, it was the evidence presented throughout the conference that decentralized identity isn’t just the future, it is the NOW. For example, only an hour after Andre’s keynote, Kristina Yasuda, Senior Identity Standards Architecture at Microsoft, gave an entire talk extolling the virtues of verifiable credentials (VCs) without even mentioning Microsoft’s own VC products. (She also didn’t mention that she is the new co-chair of the new W3C Verifiable Credentials 2.0 Working Group along with Brent Zundel of Avast).
Shortly after Kristina’s session, Brent and Drummond Reed gave a presentation on how the SSI model of digital wallets and VCs can and should be integrated with existing identity and access management (IAM) systems. Their goal was to dispel any notion that “rip and replace” was necessary to start using VCs and the ToIP stack.
But the most resounding endorsement of VCs came when Alex Simons, Microsoft’s Corporate Vice President of Identity and Network Access gave the opening keynote on the second day. He not only spent the entire first half of his talk explaining why VCs were the headline new feature of the Microsoft Entra product suite, but then invited Kristina to give a live demo of VC interop between Microsoft, Ping, Workday, IBM, and MATTR. For more on the specific interop profile they were using, see this blog post from Microsoft decentralized identity product manager Ankur Patel.
On Thursday, ToIP Steering Committee member Mike Vesey, CEO of IdRamp presented several use cases in his session “Establishing Trust with Decentralized Identity Networks, Verifiable Credentials, and Zero Trust”. Mike shared several decentralized identity solutions operating in production today, including:
- “Zoom Bouncer”, a new meeting security application now available in the Zoom public app store that allow meeting hosts to use verifiable credentials and biometrics to protect virtual meetings from zoom bombing.
- The North Dakota Department of Education decentralized identity initiative shows how verifiable credentials are being used for decentralized verification of student learner records for graduating students.
Mike also gave a demo of the IdRamp zero code orchestration platform that allows issuance of verifiable credentials from any traditional IAM system and verification with any traditional relying party service—an entire journey that can be implemented in just a few minutes without any code. “IdRamp has been providing decentralization for a few years now.” states Mike Vesey, “The IdRamp platform provides a seamless bridge from centralized identity systems into decentralized credential based authentication and access control. It was inspiring to hear that same vision being shared by the largest IAM organizations in the world. The future of identity is decentralized and ToIP is playing a major role in guiding organizations on their journey into decentralized zero trust protection.”
Judith Fleenor, Director of Strategic Engagement at the Trust Over IP Foundation, agrees: “It’s exciting to see live use cases of verifiable credentials across various sectors of government and industry. It is equally exciting to see organizations such as our Steering Committee members IdRamp and Monokee making integration with traditional IAM a breeze through their innovative system integration platforms and consulting services.”
Another key theme throughout the conference was FIDO2 passkeys. At least a half-dozen sessions were focused on this topic—not surprising given the announcements from Apple, Google, Mozilla, and the FIDO Alliance earlier this spring—and that Identiverse focuses on an enterprise IAM-centric audience where solutions to multi-factor and passwordless authentication have been sought after for two decades.
Overall, the attendees from ToIP agreed that this Identiverse took a strong step in the direction of ToIP—and it made it even more important that we push forward with our work of completing the full definition of the ToIP stack.
If you’d like to participate in ToIP’s efforts to further define a complete governance and technical architecture for interoperable digital trust, join us by becoming a member.
